
VPN is a basic networking construct when it comes to connecting multiple sites privately. Be it a private network connection from one on-premise site to another on-prem site, or a connection from an on-prem site to VMware Cloud on AWS SDDC (or vice versa), or even to establish private connections between VMware Cloud on AWS SDDC to another VMware Cloud on AWS SDDC.
VMware Cloud on AWS SDDC supports two types of Layer 3 IPSec VPN; namely: Route based VPN and Policy based IPSec VPN.
Route Based VPN
Route based VPNs in VMware Cloud on AWS SDDC uses an IPsec protocol to secure traffic and the Border Gateway Protocol (BGP) to discover and propagate routes as new networks are created. To create a route-based VPN, we need to configure BGP information for the local (Cloud SDDC) and remote (on-premises) endpoints, then specify tunnel security parameters for the SDDC end of the tunnel.
Policy Based VPN
Policy-based VPNs in VMware Cloud on AWS SDDC uses an IPsec protocol to secure traffic. To create a policy-based VPN, we ned to configure the local (SDDC) endpoint, then configure a matching remote (on-premises) endpoint. Because each policy-based VPN must create a new IPsec security association for each network, an administrator must update routing information on premises and in the SDDC whenever a new policy-based VPN is created. A policy-based VPN can be an appropriate choice when you have only a few networks on either end of the VPN, or if your on-premises network hardware does not support BGP (which is required for route-based VPNs).
Either of these IPSec VPNs can connect to SDDCs via Internet. While Policy based VPNs are more suited for smaller private networks, a Route based VPN (which also supports connection to SDDCs over AWS Direct Connect) is preferred in enterprise environments with multiple networks.
In this article we'll primarily be focusing on Policy based IPSec VPN. We will connect two VMware Cloud on AWS SDDCs with each other using Policy based IPSec VPN and send traffic between two Virtual Machines sitting on a separat private networks sitting on these two Cloud SDDCs.
Let's get started.
- Log on to the first VMware
- Log on to the VMC Console at https://vmc.vmware.com.
Select Networking & Security > VPN > Policy Based. - Click ADD VPN and give the new VPN a name similar to "SDDC1 to SDDC2”
- Select Public IP Address as your Local IP Address for the VPN.
- Enter the Remote Public IP address of your assigned target SDDC (Get this information from the other SDDC - SDDC2 in this case)
- Skip this Step If your on-premises gateway is behind a NAT device, enter the gateway address as the Remote Private IP. This IP address must match the local identity (IKE ID) sent by the on-premises VPN gateway. If this field is empty, the Remote Public IP field is used to match the local identity of the on-premises VPN gateway. Note: We will not be performing this step since the MGW and CGW (Compute and Management gateways are not behind a NAT)
- Specify the Remote Networks that this VPN can connect to. In this step enter the remote private network of your paired SDDC2 - For Example : 10.2.0.0/16.
- Specify the Local Networks that this VPN can connect to. For this step enter your local private network where your Virtual Machine resides - For Example: 10.10.0.0/16.
Configure Advanced Tunnel Parameters:
Tunnel Encryption: AES 256
Tunnel Digest Algorithm: SHA 2
Perfect Forward Secrecy: Enabled
Preshared Key: Passw0rd
IKE Encryption: AES 256
IKE Digest Algorithm: Sha 2
IKE Type: IkE V2 Diffie Hellman: Group 14 - Click Save
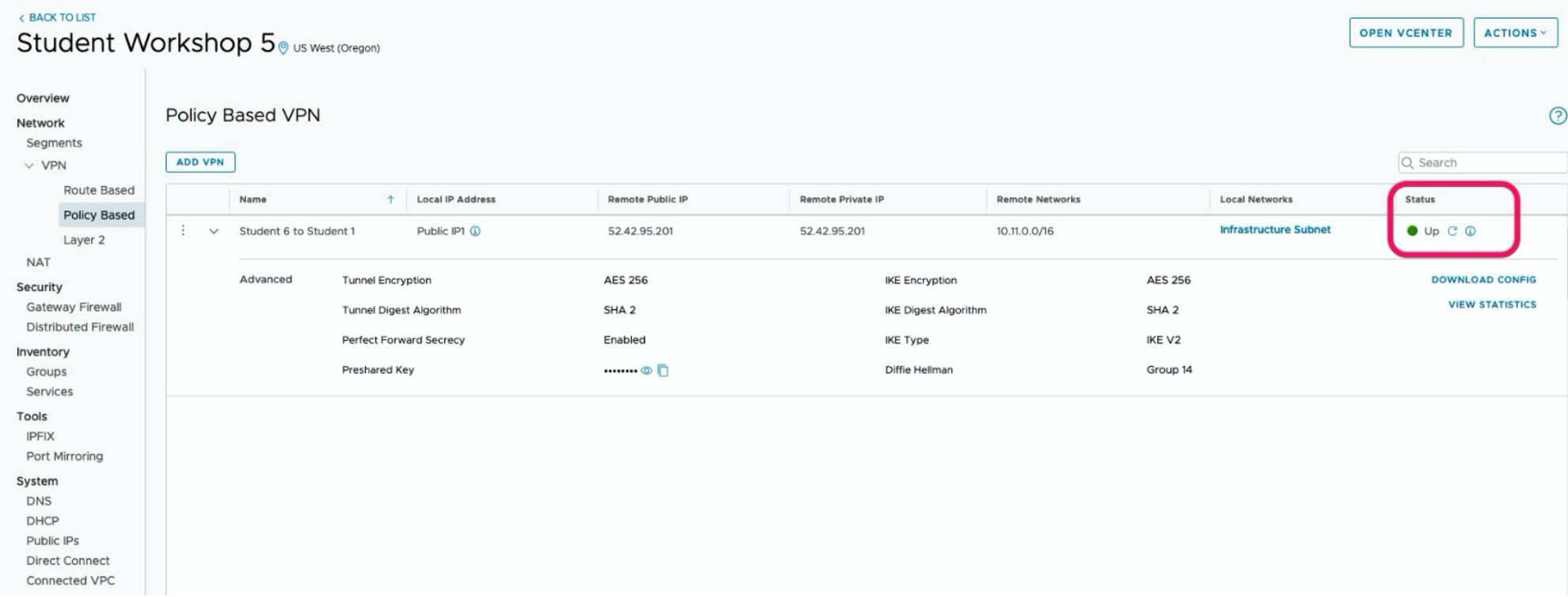
Results The VPN creation process might take a few minutes. If the VPN was configured correctly on both sides the status should be “up”.
VPN Setup Complete Image
Satya is an experienced IT professional with a demonstrated history of working in the Information Technology with years of experience in multiple industry verticals. He currently works for VMware as Staff Cloud Solutions Architect. He is skilled in designing and implementing Enterprise Application Suite in Public, Private and Hybrid cloud infrastructure including AWS, VMware, VMware Cloud on AWS, Microsoft AZure, Google Cloud and the like.
Get connected with Satya:



0 Comments