Hi friends 👋, let's continue building our EKS environment by deploying managed EKS Node Groups in AWS.
Continuing on from where we left before in Part 1 , we will now use a Cloudformation template to deploy EKS Addons ( CNI plugin ) and then a managed Node Group. To enable pod networking, we need to deploy a networking layer into our EKS environment.
Lets deploy the following cloudformation template which will deploy an addon - VPC CNI Plugin to our EKS environment,
---
AWSTemplateFormatVersion: 2010-09-09
Description: Deploy EKS Addons
Resources:
VpcCni:
Type: AWS::EKS::Addon
Properties:
AddonName: vpc-cni
AddonVersion: v1.7.10-eksbuild.1
ClusterName: !ImportValue pras-kube-cluster-name ## Replace this with your cluster name
ResolveConflicts: OVERWRITE
Tags:
- Key: created_by
Value: pras
- Key: eks_addon
Value: True
Run the following command to deploy the addon,
aws cloudformation deploy \
--s3-bucket pras-cloudformation-artifacts-bucket \
--template-file cloudformation/eks-addons.yaml \
--stack-name pras-eks-addons \
--capabilities CAPABILITY_NAMED_IAM \
--no-fail-on-empty-changeset \
--tags \
Name='Kubernetes Cluster Resources - EKS Addons'Verify that the cloudformation stack created fine,
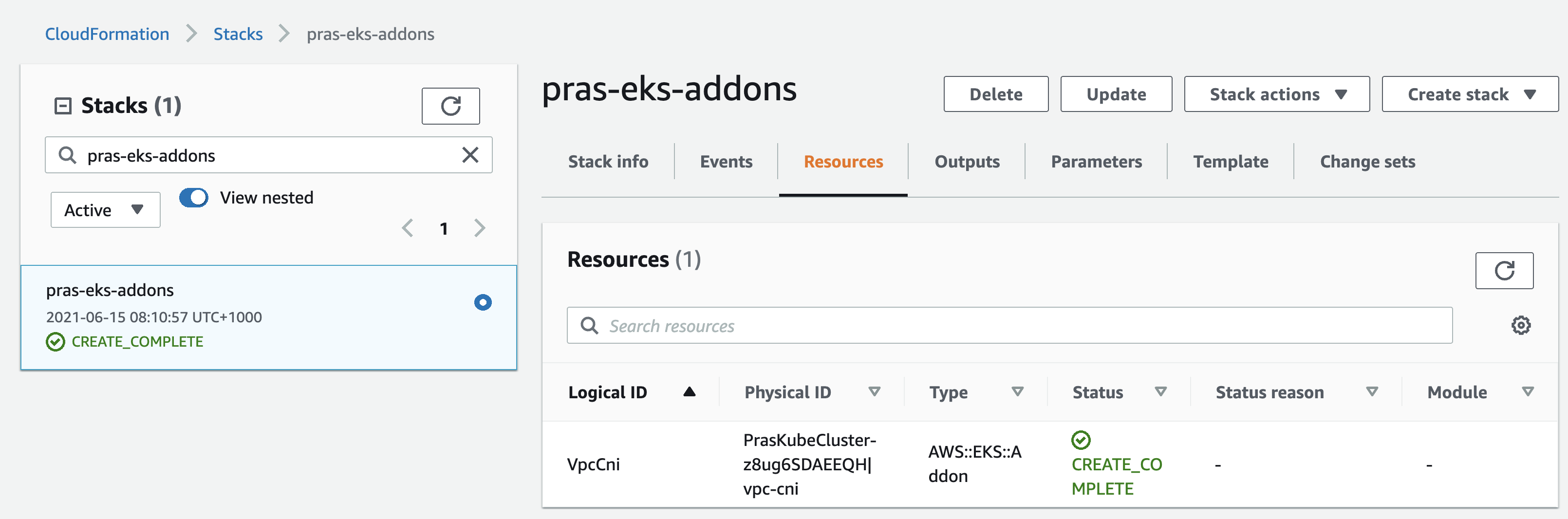
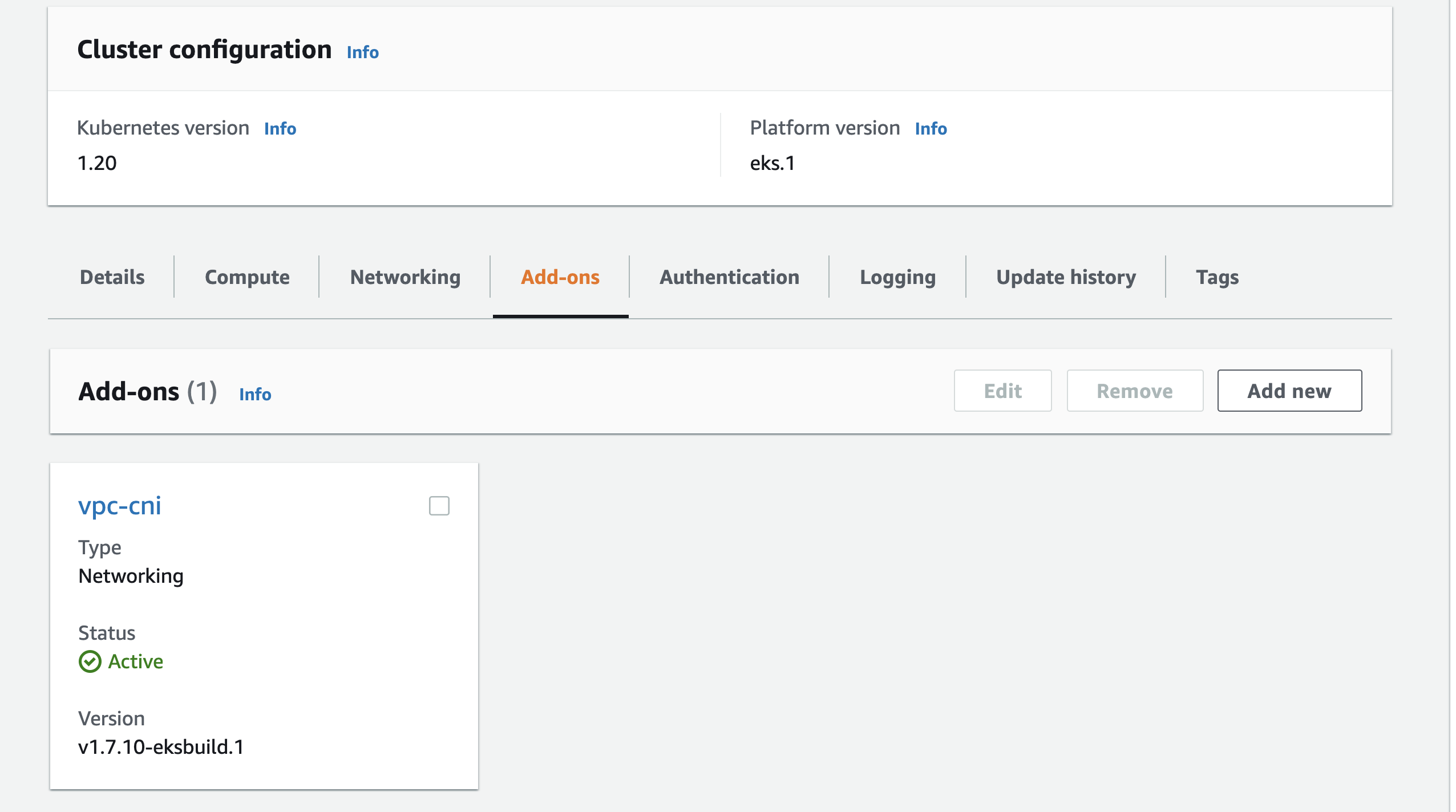
Verify from the EKS Console that the addon has been successfully deployed,
Now that we have pod networking ready, we can go ahead and deploy an EKS managed Nodegroup. Let's look at the cloudformation template below,
---
AWSTemplateFormatVersion: 2010-09-09
Description: Deploy Managed Kubernetes Resources - Worker Nodes
Resources:
PrasKubeNodeGroupRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service:
- ec2.amazonaws.com
Action:
- sts:AssumeRole
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy
- arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly
- arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy
PrasKubeClusterNodegroupFleet:
Type: AWS::EKS::Nodegroup
Properties:
ClusterName: !ImportValue pras-kube-cluster-name
NodeRole: !GetAtt PrasKubeNodeGroupRole.Arn
InstanceTypes:
- t3.large
CapacityType: SPOT
ScalingConfig:
MinSize: 1
DesiredSize: 1
MaxSize: 3
Labels:
pras-kube-node-group: True
app: cool-app
Subnets:
- Fn::ImportValue: pras-vpc-private-subnet-a-id
- Fn::ImportValue: pras-vpc-private-subnet-b-id
Tags: {"created_by": "pras", "purpose": "learning", "eks_role": "node_group"}The IAM Role is for NodeGroup to perform certain actions like joining the cluster, communicating with the cluster and reading from container registry to deploy containers into pods. Find out more on Node IAM permissions here . I am also making use of SPOT instances as this is my test environment, you surely don't want to use SPOT when running production workloads. Learn more about spot instances here .
Use the following AWS cli command to deploy Node Group via CloudFormation,
aws cloudformation deploy \
--s3-bucket pras-cloudformation-artifacts-bucket \
--template-file cloudformation/eks-nodegroup.yaml \
--stack-name pras-eks-nodegroup \
--capabilities CAPABILITY_NAMED_IAM \
--no-fail-on-empty-changeset \
--tags \
Name='Kubernetes Cluster Resources - Worker Nodes'Verify from Cloudformation Console that the stack has been created successfully,
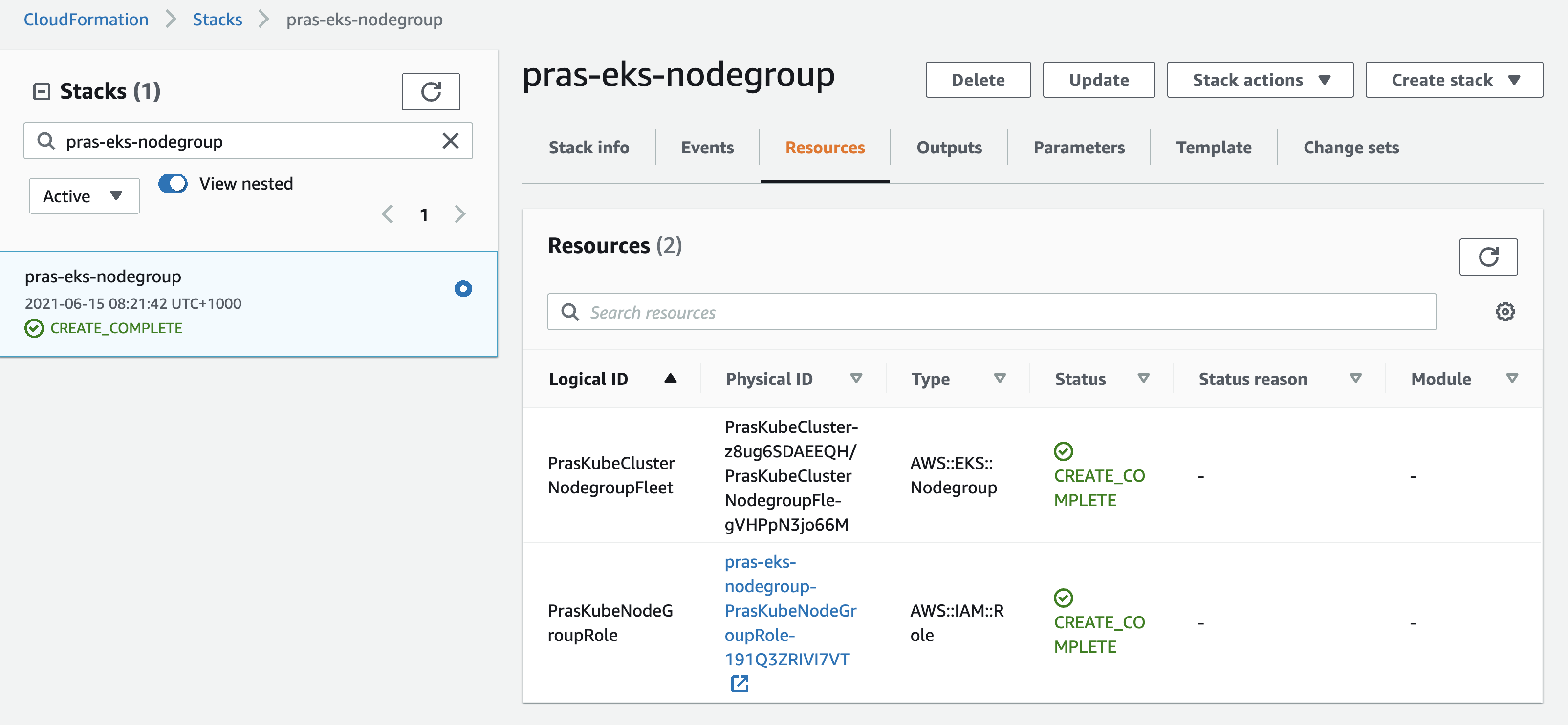
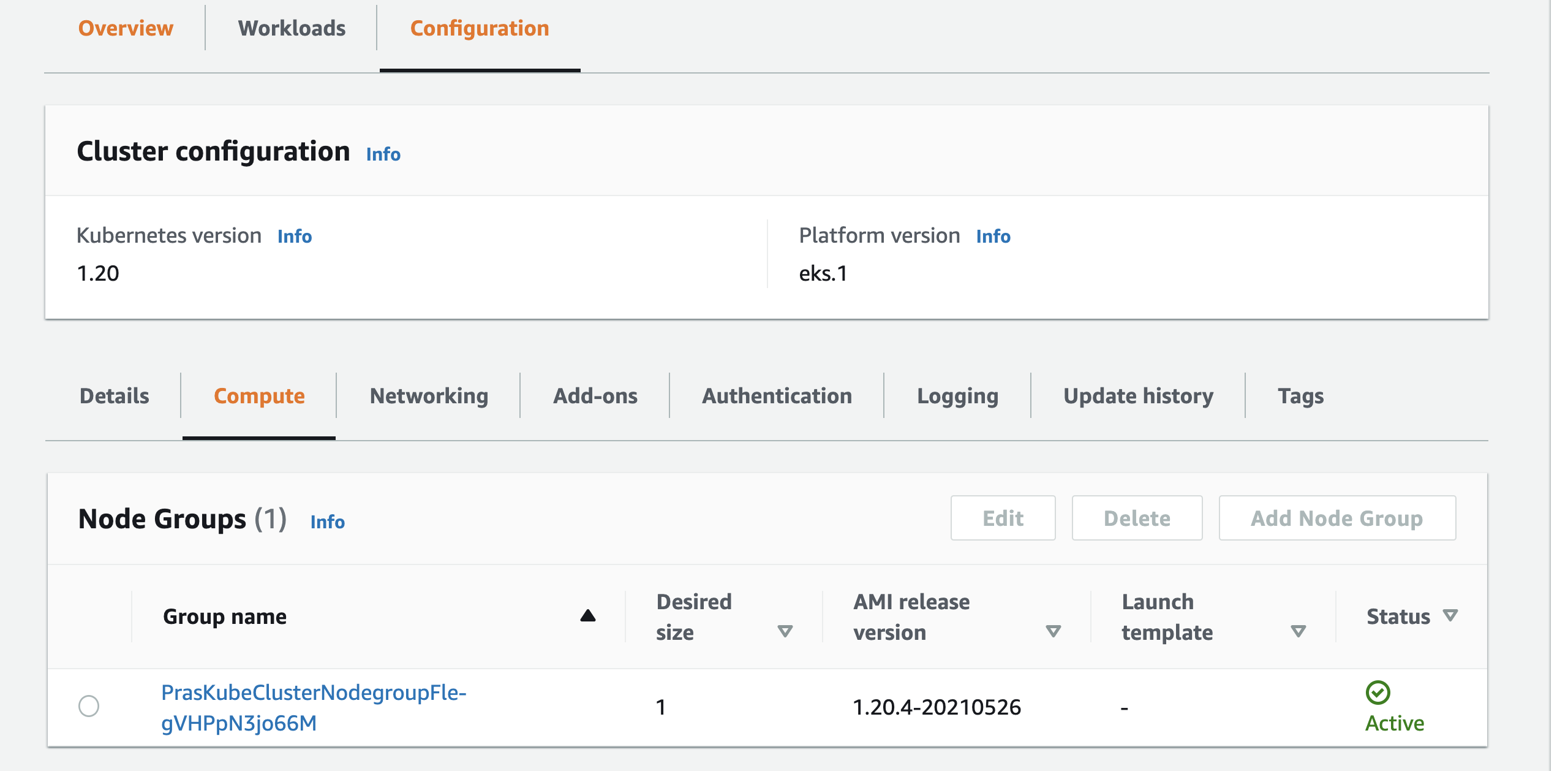
Verify from EKS Console that the Node Group has been created,
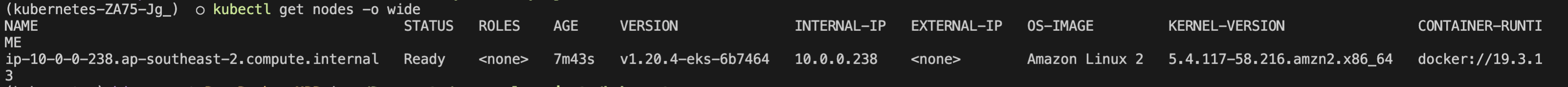
Run kubectl get nodes -o wide to get a list of nodes,
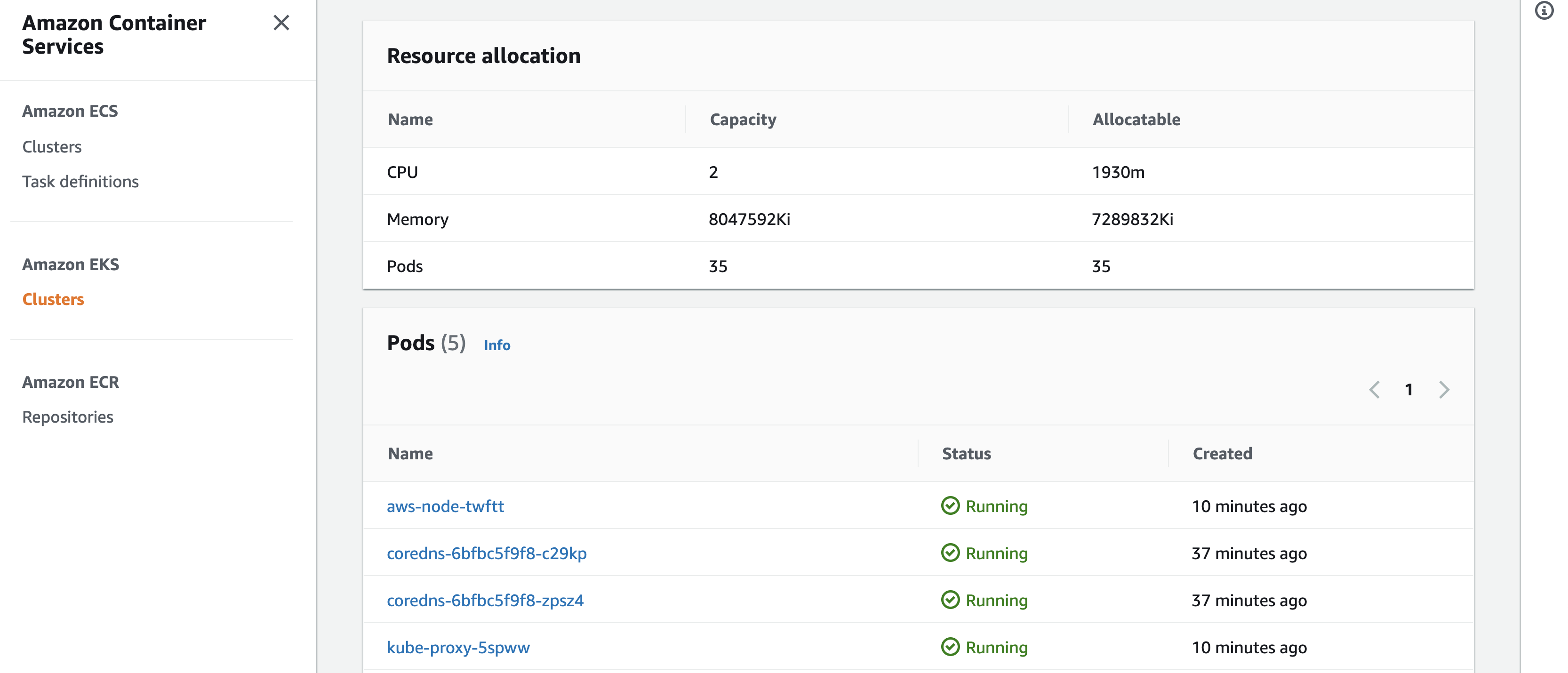
Click on the node from EKS console to see more information like what pods are currently deployed on the node, resource requirements and so on,
Congratulations, we have successfully deployed a managed EKS Environment on AWS. We first created the cluster resources and the cluster itself, eks addon to support pod networking and finally managed node group as our worker nodes. We are now ready to run applications on the managed EKS environment 🎉



0 Comments