Knowledge Academy
Advancing Knowledge, Transforming Lives
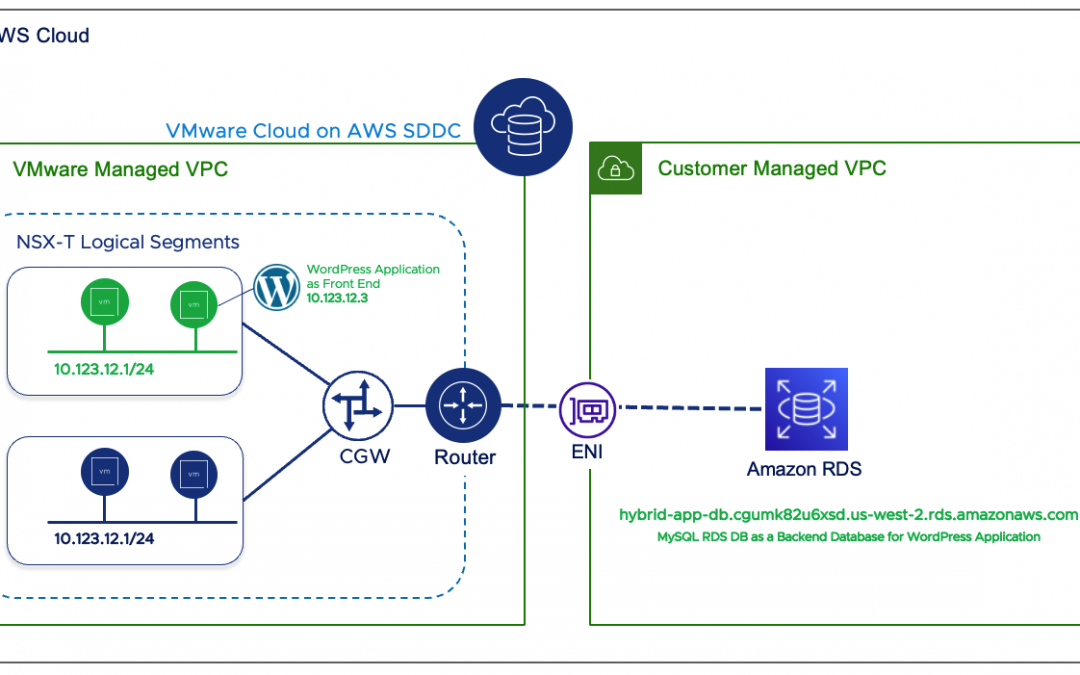
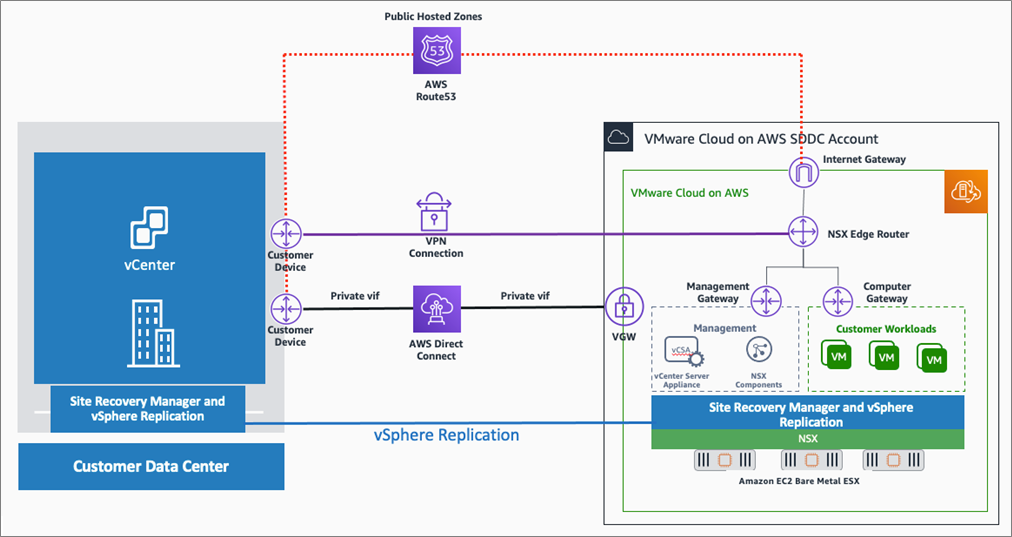
Integrating Amazon RDS with workloads running in VMware Cloud on AWS
VMware Cloud on AWS (VMC on AWS) is VMware’s flagship Public/Hybrid Cloud offering which our global customers can use around the world. VMC on AWS is the most matured cloud offering from VMware with all the enterprise features that our customers...
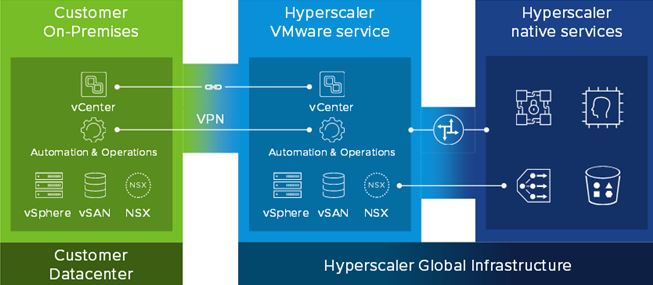
A Journey Towards Multi-Cloud – VMware Cloud Offerings
Let's discuss on the VMware Cloud Offerings one by one that provides the customer with Hybrid Capabilities and enable the fastest path to cloud without the need for refactoring or replatforming their applications. VMware Cloud comprises of all the...
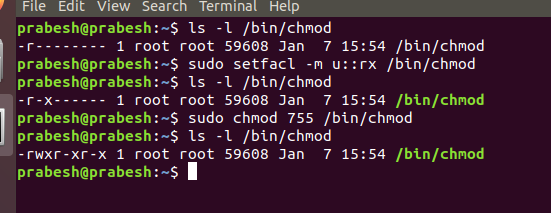
What to do when you can’t chmod chmod?
When you cannot chmod chmod? What to do? This might help to re-instate permission back. Here are following techniques where you can use chmod to change permission when chmod itself is not executable. Using rsync: The first technique is to use rsync...
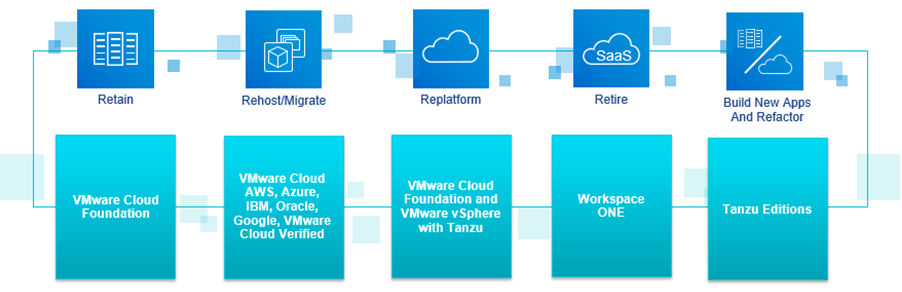
A Journey to Multi-Cloud – Cloud Migration
This is Girish Raja back with the 3rd chapter of my blog series on "A Journey Towards Multi-Cloud" which will focus on Migration aspects of VMware Cloud and how well does VMware align with the 5Rs of Cloud Migration. Let us first start with the...
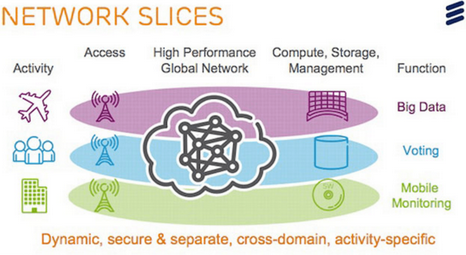
Network Slicing
Customers come to ISP’s with different requirements. It is not easy to cater the services.5G is promising with high quality transmission and more data with huge increase in the number of connections to support the needs of industry with respect to...
A Journey to Multi-Cloud – Disaster Recovery
This is Girish Raja here again resuming the series about VMware Cloud from where I left in my previous journal. We saw in our previous blog how VMware Cloud addresses the challenges faced by enterprise in their adoption towards multi-cloud, land...
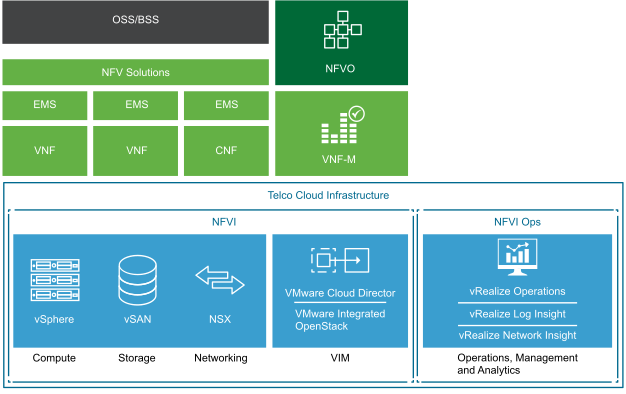
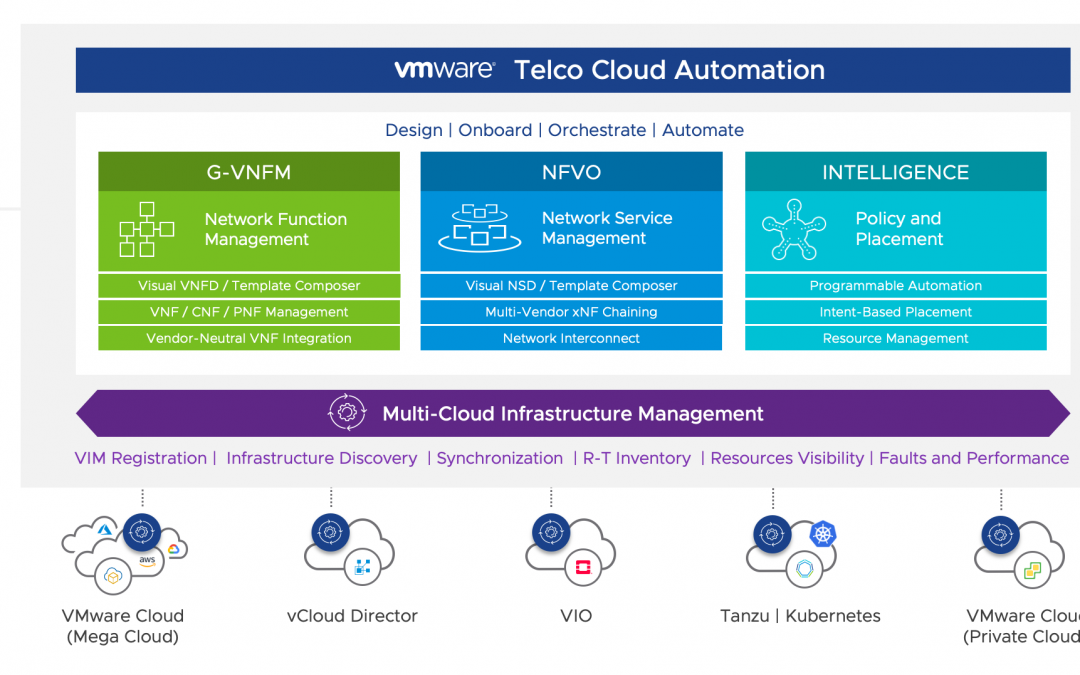
Design your NFVi Performance
Author's Quick Intro: Praveen Batta has 16 years of experience in various technology stacks including Kubernetes, VMware cloud with SDN integrations of VMware NSX, Juniper Contrail, Linux, Storage and Openstack cloud. Praveen has been serving in...

How does Linux kernel decide which process to kill when there is no memory left on the system?
Linux kernel has a feature or application called OOM Killer. It kills the process whenever it is out of memory. OOM decides which process to kill based on a score that it calculates which is called oom_score. You can find oom_score for each process...

A Journey to Multi-Cloud – Cloud Migration
This is Girish Raja, Staff Cloud Solution Architect with VMware starting this blog series on Multi-Cloud and VMware Cloud offerings towards Multi-Cloud which should make cloud adoption faster and easier. I believe this information will be...
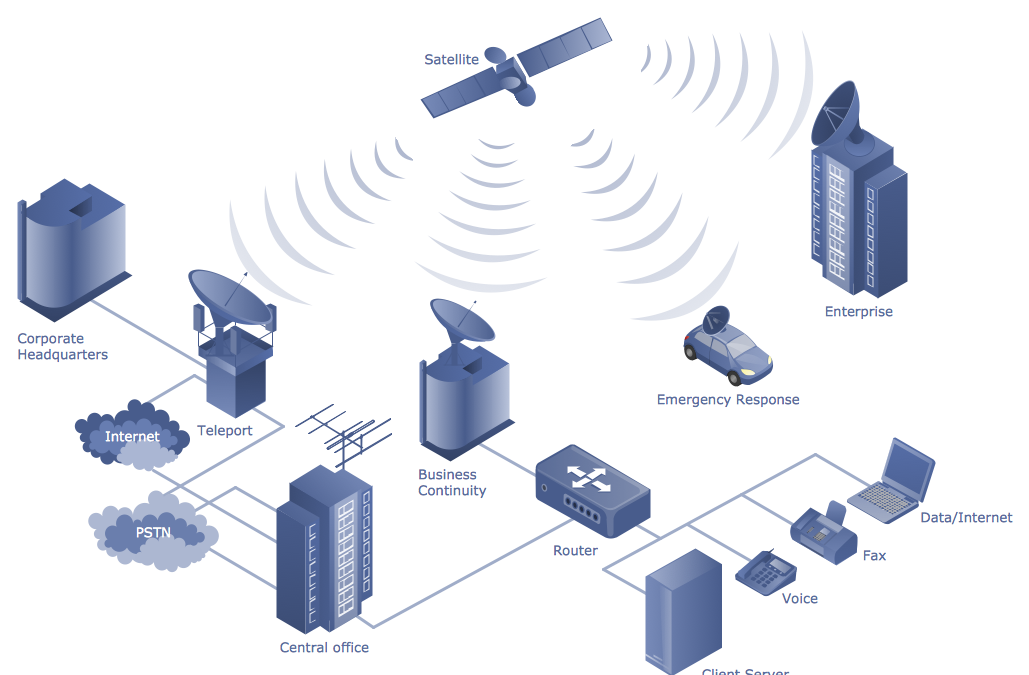
Evolution of Telecommunications – Part 2
Introduction: This blog is continuation of the blog https://knowledgeacademy.io/evolution-of-telecommunications/. With this blog let’s understand "How VMware is contributing to achieve Telecommunications Challenges." To provide the acceleration...
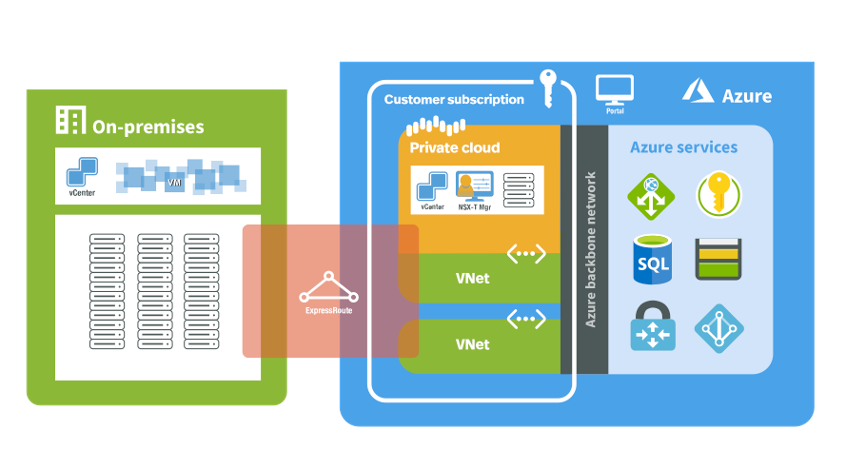
Integrating Azure Application Gateway for Load Balancing workloads in Azure VMware Solutions (AVS)
Brief Introduction to Azure VMware SolutionWith Azure VMware Solution (AVS), now available globally in Microsoft Azure as a native Azure Cloud offering from Microsoft, customers around the globe can enjoy the same world class industry leading...
Evolution of Telecommunications
Introduction: Praveen Batta with 16 years of experience in various technologies. Started my carrier with Linux administration and extended to Storage, Open stack cloud, VMware cloud with SDN integrations of Juniper Contrail and VMware NSX. Worked...
WINDOWS SERVER 2019: A STEP-BY-STEP TUTORIAL ON SYSTEM CENTER CONFIGURATION MANAGER (SCCM) WITH PRACTICAL EXAMPLE – PART 2
In the previous article, we looked at installing Windows Server 2019 in a virtual box environment. In this article, we will be configuring Active Directory, DNS AND DHCP for System Center Configuration manager (SCCM). Active Directory (AD) is a...
Azure Virtual Desktop Use Cases and Benefits
What is Azure Virtual Desktop? Azure Virtual Desktop (formerly Windows Virtual Desktop) is a Remote Desktop Computer service with latest Windows Operating System and Office 365 ProPlus installed. It's a platform where anyone can access their...

VPC Basics
Amazon VPC (Virtual Private Cloud) is a virtual network infrastructure like a physical datacenter, which provides network connectivity to all the resources deployed in that VPC. There are few key concepts for VPCs which you should understand: VPC-...

VPC Ingress Routing
The VPC incoming network traffic would have to be forwarded to on-premises appliance or firewall in order to inspect the traffic and routed back to VPC which is not an ideal solution, it adds latency and complexity.

How do I configure a site-to-site VPN to between AWS VPN and Openswan Instance
I want to connect to my Amazon Virtual Private Cloud (Amazon VPC) from my on-premises. How can I configure Openswan for this purpose?
Windows Server 2019: a step-by-step tutorial on System Center Configuration Manager (SCCM) with practical example
This is part 1 of a 4 part series where we will configure System Center Configuration manager (SCCM) in a Windows Server 2019 environment. SCCM enables the management, deployment and security of devices and applications across an enterprise. Most...

Integrating Amazon RDS with workloads running in VMware Cloud on AWS
VMware Cloud on AWS (VMC on AWS) is VMware’s flagship Public/Hybrid Cloud offering which our global customers can use around the world. VMC on AWS is the most matured cloud offering from VMware with all the enterprise features that our customers...

A Journey Towards Multi-Cloud – VMware Cloud Offerings
Let's discuss on the VMware Cloud Offerings one by one that provides the customer with Hybrid Capabilities and enable the fastest path to cloud without the need for refactoring or replatforming their applications. VMware Cloud comprises of all the...

What to do when you can’t chmod chmod?
When you cannot chmod chmod? What to do? This might help to re-instate permission back. Here are following techniques where you can use chmod to change permission when chmod itself is not executable. Using rsync: The first technique is to use rsync...

A Journey to Multi-Cloud – Cloud Migration
This is Girish Raja back with the 3rd chapter of my blog series on "A Journey Towards Multi-Cloud" which will focus on Migration aspects of VMware Cloud and how well does VMware align with the 5Rs of Cloud Migration. Let us first start with the...

Network Slicing
Customers come to ISP’s with different requirements. It is not easy to cater the services.5G is promising with high quality transmission and more data with huge increase in the number of connections to support the needs of industry with respect to...

A Journey to Multi-Cloud – Disaster Recovery
This is Girish Raja here again resuming the series about VMware Cloud from where I left in my previous journal. We saw in our previous blog how VMware Cloud addresses the challenges faced by enterprise in their adoption towards multi-cloud, land...

Design your NFVi Performance
Author's Quick Intro: Praveen Batta has 16 years of experience in various technology stacks including Kubernetes, VMware cloud with SDN integrations of VMware NSX, Juniper Contrail, Linux, Storage and Openstack cloud. Praveen has been serving in...

How does Linux kernel decide which process to kill when there is no memory left on the system?
Linux kernel has a feature or application called OOM Killer. It kills the process whenever it is out of memory. OOM decides which process to kill based on a score that it calculates which is called oom_score. You can find oom_score for each process...

A Journey to Multi-Cloud – Cloud Migration
This is Girish Raja, Staff Cloud Solution Architect with VMware starting this blog series on Multi-Cloud and VMware Cloud offerings towards Multi-Cloud which should make cloud adoption faster and easier. I believe this information will be...

Evolution of Telecommunications – Part 2
Introduction: This blog is continuation of the blog https://knowledgeacademy.io/evolution-of-telecommunications/. With this blog let’s understand "How VMware is contributing to achieve Telecommunications Challenges." To provide the acceleration...

Integrating Azure Application Gateway for Load Balancing workloads in Azure VMware Solutions (AVS)
Brief Introduction to Azure VMware SolutionWith Azure VMware Solution (AVS), now available globally in Microsoft Azure as a native Azure Cloud offering from Microsoft, customers around the globe can enjoy the same world class industry leading...

Evolution of Telecommunications
Introduction: Praveen Batta with 16 years of experience in various technologies. Started my carrier with Linux administration and extended to Storage, Open stack cloud, VMware cloud with SDN integrations of Juniper Contrail and VMware NSX. Worked...
WINDOWS SERVER 2019: A STEP-BY-STEP TUTORIAL ON SYSTEM CENTER CONFIGURATION MANAGER (SCCM) WITH PRACTICAL EXAMPLE – PART 2
In the previous article, we looked at installing Windows Server 2019 in a virtual box environment. In this article, we will be configuring Active Directory, DNS AND DHCP for System Center Configuration manager (SCCM). Active Directory (AD) is a...
Azure Virtual Desktop Use Cases and Benefits
What is Azure Virtual Desktop? Azure Virtual Desktop (formerly Windows Virtual Desktop) is a Remote Desktop Computer service with latest Windows Operating System and Office 365 ProPlus installed. It's a platform where anyone can access their...

VPC Basics
Amazon VPC (Virtual Private Cloud) is a virtual network infrastructure like a physical datacenter, which provides network connectivity to all the resources deployed in that VPC. There are few key concepts for VPCs which you should understand: VPC-...

VPC Ingress Routing
The VPC incoming network traffic would have to be forwarded to on-premises appliance or firewall in order to inspect the traffic and routed back to VPC which is not an ideal solution, it adds latency and complexity. A route table is associated with...

How do I configure a site-to-site VPN to between AWS VPN and Openswan Instance
What is Open Swan?Openswan has been the de-facto Virtual Private Network software for the Linux community since 2005. If you are running Fedora, Red Hat, Ubuntu, Debian (Wheezy), Gentoo, or many others, it is already included in your distribution!...
Windows Server 2019: a step-by-step tutorial on System Center Configuration Manager (SCCM) with practical example
This is part 1 of a 4 part series where we will configure System Center Configuration manager (SCCM) in a Windows Server 2019 environment. SCCM enables the management, deployment and security of devices and applications across an enterprise. Most...




Recent Comments