VMware Cloud on AWS (VMC on AWS) is VMware’s flagship Public/Hybrid Cloud offering which our global customers can use around the world. VMC on AWS is the most matured cloud offering from VMware with all the enterprise features that our customers are used to. With VMC on AWS, VMware and AWS customers can build, manage, secure, modernize and operate VMware based workload in the cloud. VMC on AWS support all kinds of enterprise cloud computing use cases such as Cloud Migration, Cloud Bursting, Data Center (DC) Expansion, DC Extension, DC Evacuation, Virtual Desktop Infrastructure (VDI) in the Cloud, Application Modernization, Kubernetes in the Cloud and so on.
Amazon Relational Database Service (RDS) on the other hand, is one of the most popular managed Database service from Amazon Web Services (AWS). Amazon RDS currently supports most of the popular Relational Databases such as MySQL, PostgreSQL, Oracle, Microsoft SQL Server along with Amazon’s own database engines - Amazon Aurora with MySQL and PostgreSQL flavours. Customers around the world are adopting cloud databases in Amazon RDS for its simplicity, ease of use, and to off-load tedious Database maintenance responsibilities from DBAs to AWS. Amazon RDS takes care of many critical DB operations such as, upgrading, patching, High Availability, DB Resiliency, database backups to name a few.
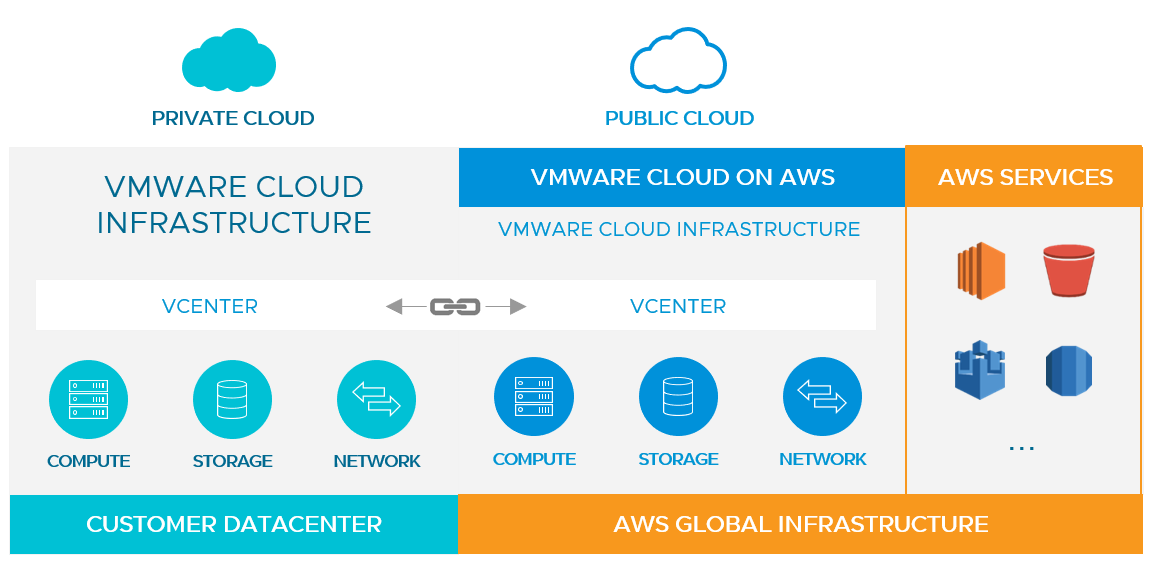
The beauty of VMC on AWS running on AWS Cloud, is its adjacency and proximity to all services from AWS. Like Amazon EC2 (Amazon’s popular Cloud Computing service), VMC on AWS is now a first-class citizen, that can integrate readily with any services in AWS. The workloads/Virtual Machines/Applications/Containers residing on VMC on AWS can quickly and easily consume AWS services such as Amazon RDS, S3, EC2, Dynamo DB, Lambda, Route53 etc. When architected appropriately, integrating these workloads with AWS services, can benefit customers from “Zero” egress cost, low latency and higher performance. Currently we are witnessing so many innovative and interesting solutions and emerging new use cases in this area, from our customers and partners around the world.
In this article, we will walk through steps to integrate Amazon RDS with workloads running on VMC on AWS SDDC. While these integrations can be done in many ways, with various networking constructs (VPC Peering, Transit Gateway etc), we will be focusing solely on integration of these services using Elastic Network Interface (ENI) or VPC Interface (as it appears on VMC on AWS Console), which is available by default when VMC on AWS Software Defined Data Center (SDDC) is spun up and customer connect their VPC (Virtual Private Cloud) with the VMC on AWS SDDC.
Little Bit on Elastic Network Interface (ENI)
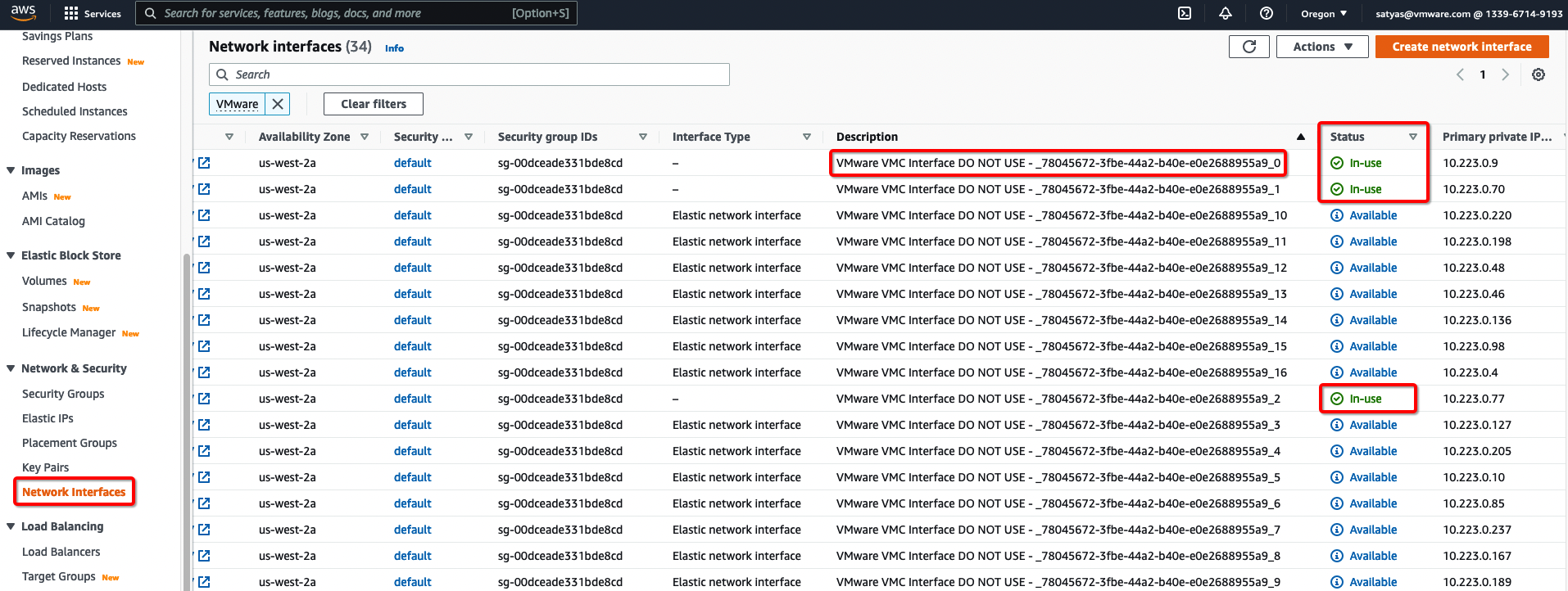
Elastic Network Interface (ENI) connects VMware Cloud on AWS and the customer’s Virtual Private Cloud (VPC). It provides a high-bandwidth, low latency connection between the Customer managed VPC and the VMware Cloud on AWS SDDC. When architected appropriately, there are no data Egress charges across the ENI within the same Availability Zone. Appropriate firewall rules can/should be created on both ends of this connection for securing workloads.
Common Use cases for this Integration:
Below are some common customer use cases that we’re currently seeing in the field where customers are integrating Amazon RDS with workloads residing on VMware Cloud on AWS SDDC:
- Integrating existing Amazon RDS Databases with VMware Workloads/Application servers residing on VMware Cloud on AWS SDDC or On-premises
- Modernizing existing databases on VMware Cloud on AWS SDDC or On-premises by moving it to Amazon RDS
- Migrating storage heavy databases from VMware Cloud on AWS SDDC or On-premises to Amazon RDS
- Building net new databases on Amazon RDS and accessing them from VMware Cloud on AWS SDDC
- Creating replicated databases between VMware Cloud on AWS SDDC and Amazon RDS
For the purpose of this article, we’ll be using WordPress application residing on Virtual Machine “linux-hybrid-app01” with IP Address 10.123.12.3 in VMC on AWS SDDC as a Front-end server and “hybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com” Amazon RDS MySQL DB Instance as a backend server.
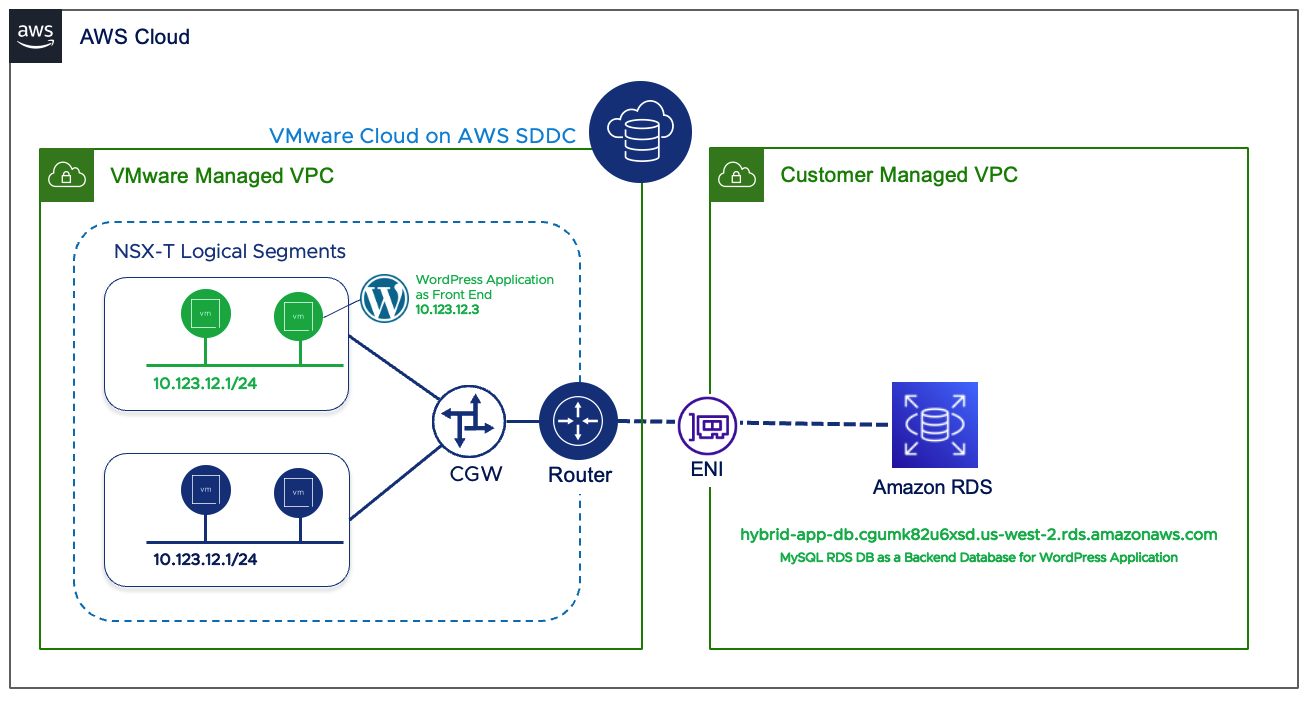
Architecture Diagram of Amazon RDS Integration with VMC on AWS SDDC
Creating Amazon RDS DB Instance:
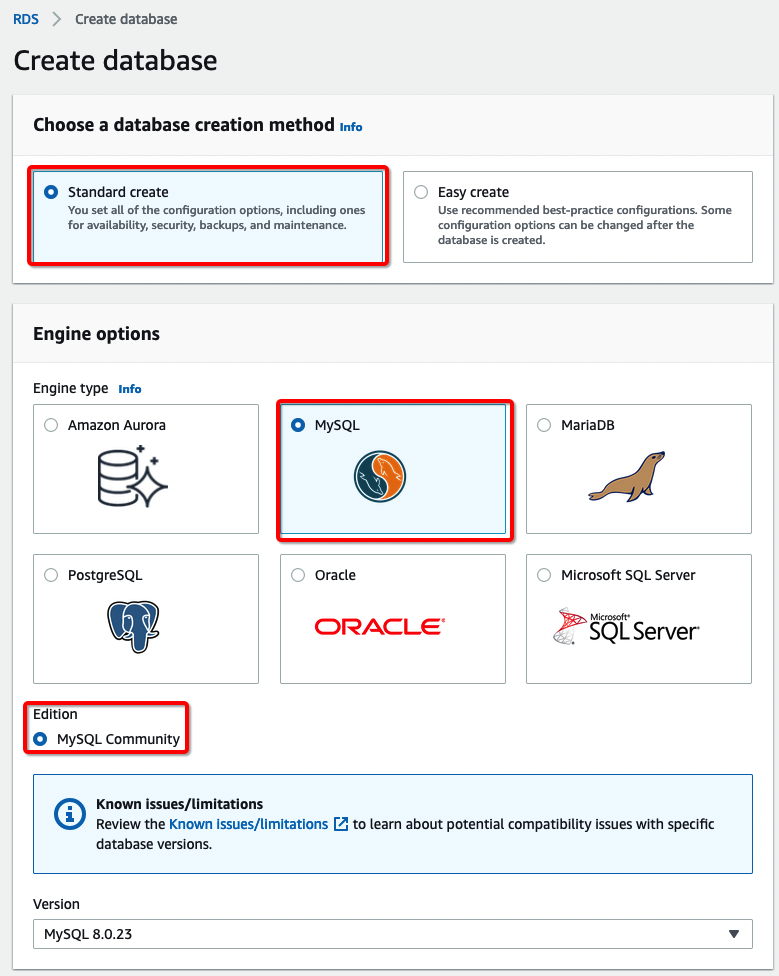
1. Create an Amazon RDS MySQL Database (DB) Instance with appropriate instance type and configuration to fit your application use case. For this example, as this is a lab/demo environment, I’ve created a simple t3.micro MySQL DB instance on the same VPC and Availability Zone (AZ) as VMware Cloud on AWS SDDC. Below is my Amazon RDS DB Instance Configuration:
b) In the “Templates” section, I’ve selected “Dev/Test” and “Single DB Instance” with a single AZ deployment.
asdasd
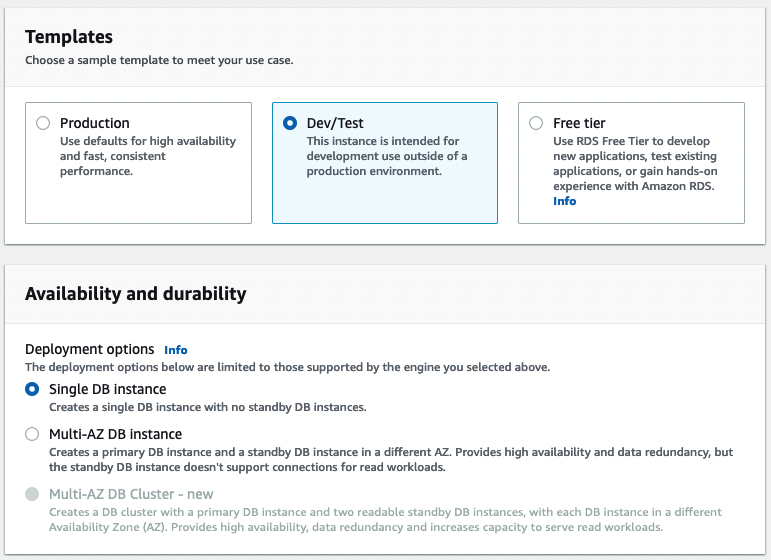
c) I’ve set the DB Instance Identifier as “hybrid-app-db” and set my Master username to “admin” with the master user password.
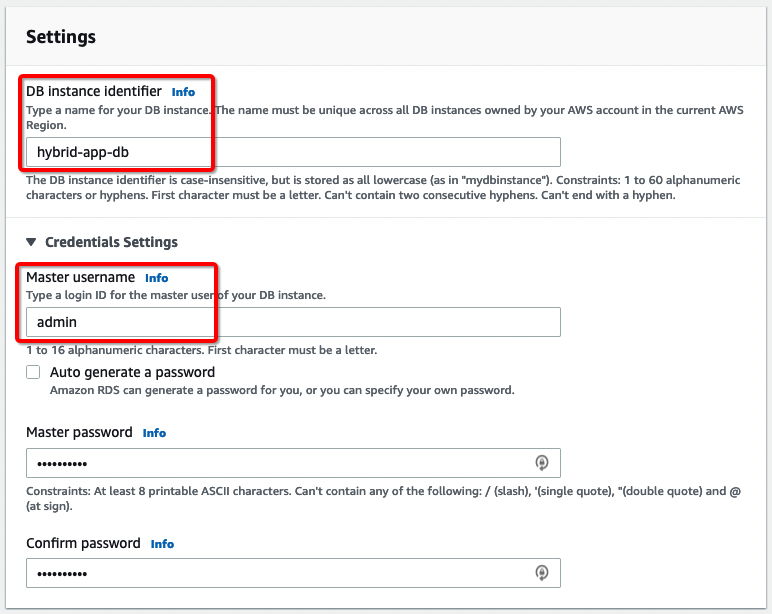
d) For Instance configuration, I’ve selected “Burstable classes – db.t3.micro” and for Storage, I’ve selected “General Purpose SSD (gp2)” with “20 GiB” Allocated storage. I’ve left Storage autoscaling to its default.
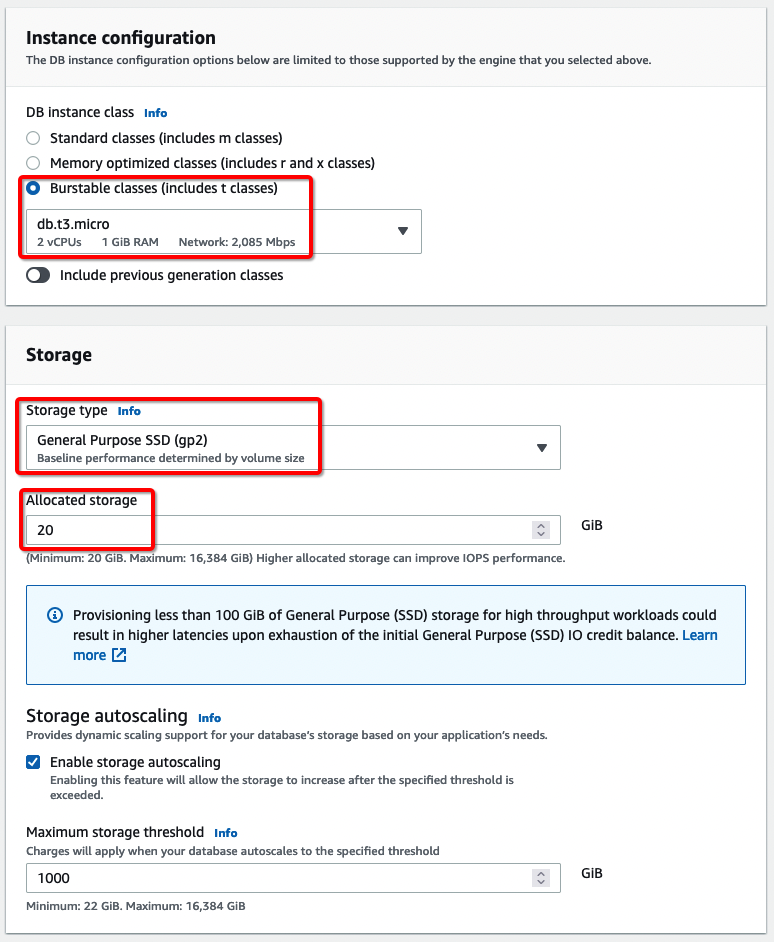
e) In the Connectivity section, I’ve selected “IPv4” for Network type, “mca-vpc-demo” for Virtual private cloud (VPC). Since I want the DB to be accessible only from private networks, I’ve selected “No” for Public Access. The DB is placed in the “us-west-2b” Availability Zone, that the same VPC and Subnet which we selected for “Connected VPC or Customer Managed VPC” when VMC on AWS SDDC was created. For Additional configuration, we left the Database port at its default value of 3306.
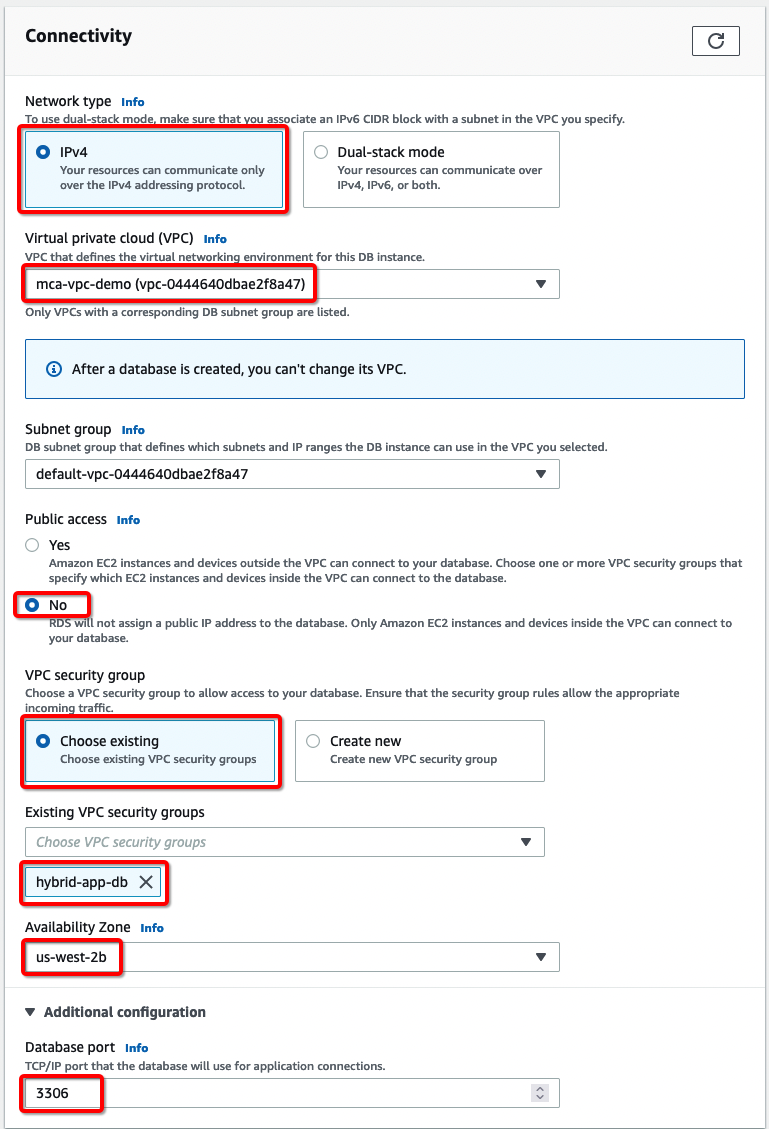
I’ve pre-created a security group called “hybrid-app-db” with appropriate security group rules to allow traffic from VMC on the AWS SDDC application segment to the Amazon RDS DB, so I chose “hybrid-app-db” for the Existing VPC security groups option. Below you can see a snapshot of Security Group Inbound rules where source “10.123.12.0/24”, which is an NSX-T segment on VMC on AWS SDDC, is allowed to connect to any instances that are associated with this “hybrid-app-db” security group
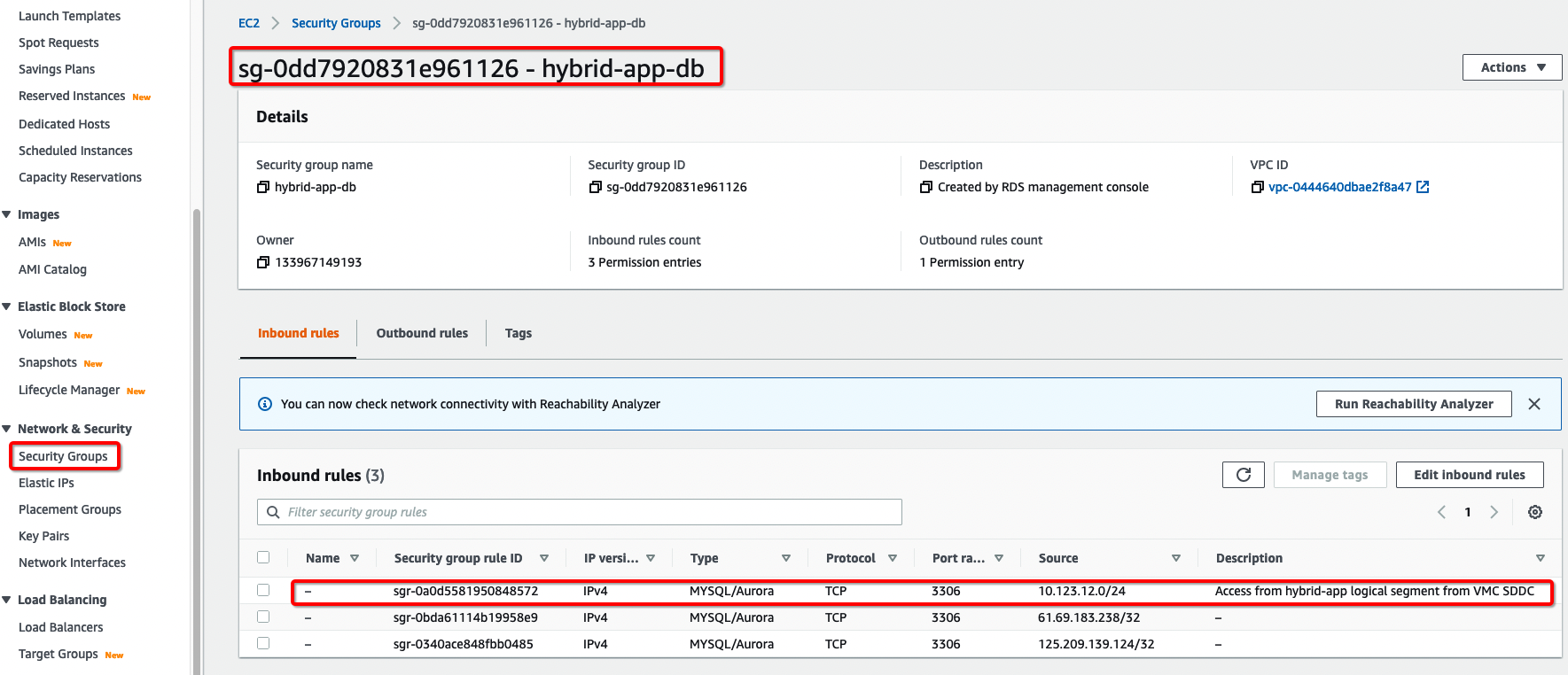
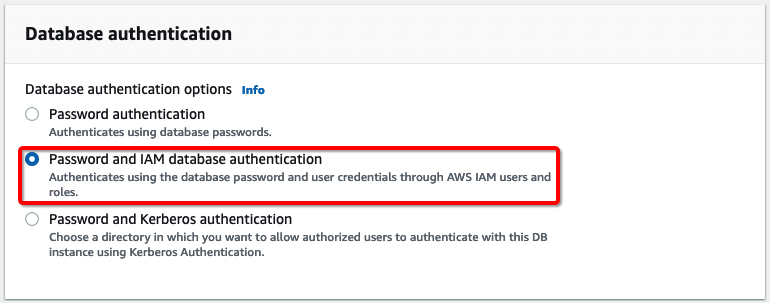
f) For Database authentication, we selected “Password and IAM authentication”
Configuring Front End Server:
2. In the vCenter management console, I’ve created a simple Debian Linux VM with Apache, MySQL Client, and other network tools installed. This Linux VM is named “linux-hybrid-app-01” and acts as an Application/Web server that is sitting on “10.123.12.0/24” NSX-T segment with an IP address of “10.123.12.3”.
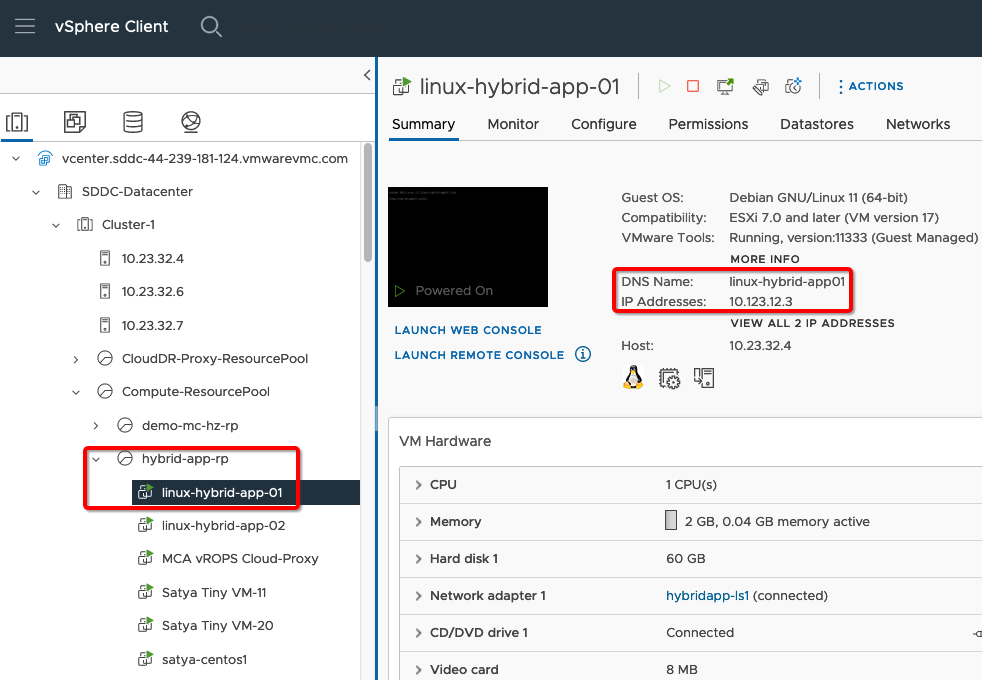
3. For ease of access and command execution on “linux-hybrid-app-01” application server, let’s make it publicly accessible by assigning it a Public IP address:
a. Log on to VMware Cloud Console and Navigate to VMC on AWS Console.
b. On the VMC on AWS SDDC Console, go to Networking & Security and click on Public IPs.
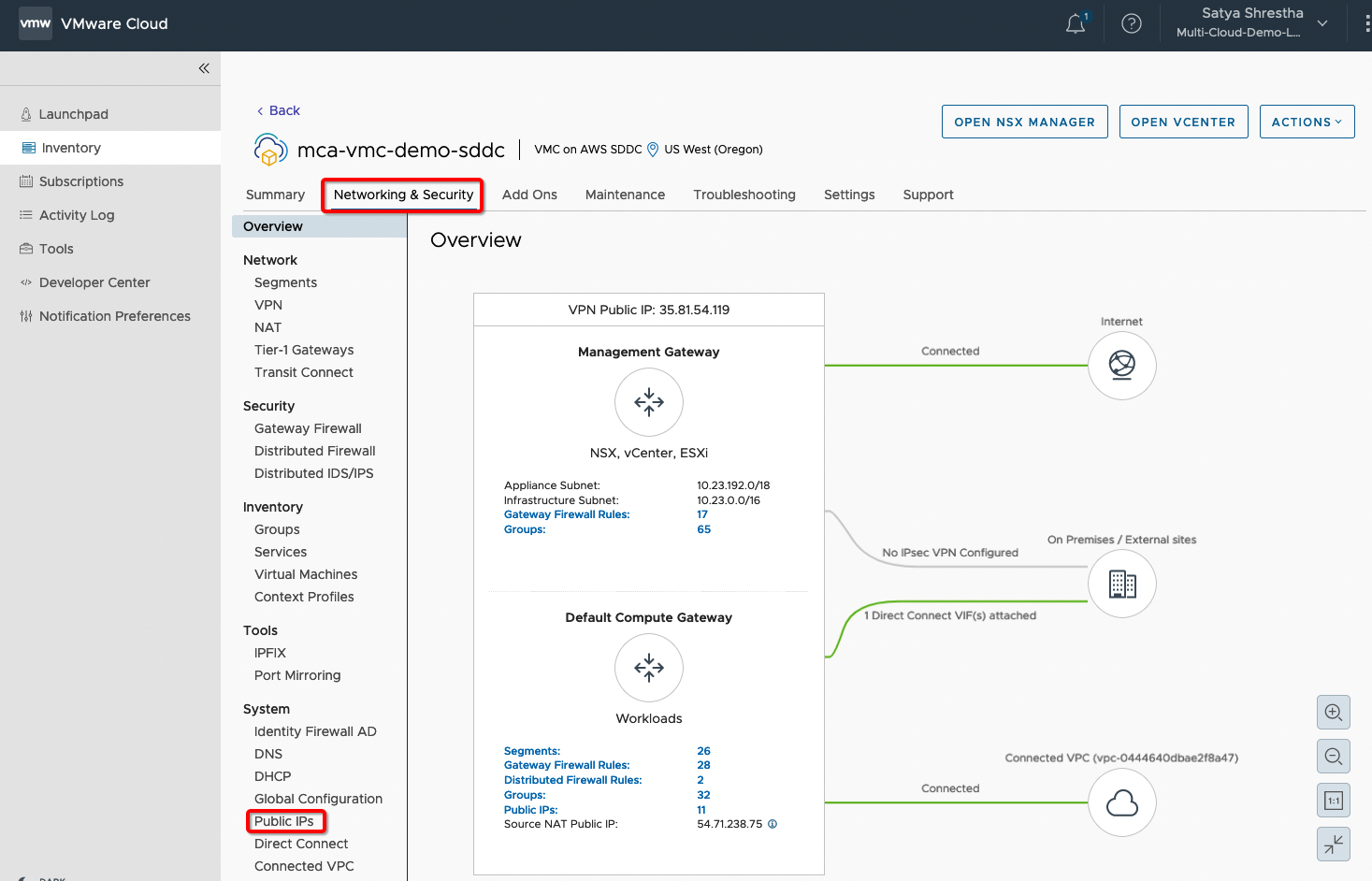
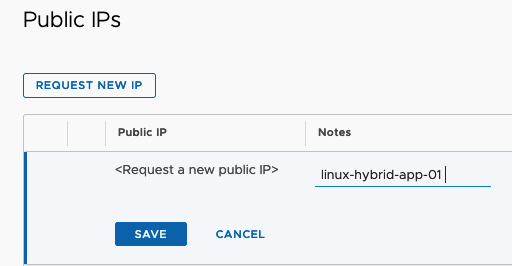
c) Request a new IP, give it appropriate Note and Save.
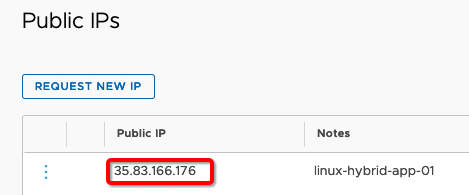
f) Create NAT rules as shown on the picture below.
4. Create appropriate firewall rules to allow incoming/outgoing traffic to the Application server. In this example, for simplicity, we’ve allowed Any Sources to go to our Logical Segment “hybrid-ap-ls” and access Any Services. You would want to lock it down tightly in your production environment. Configure Gateway Firewall Rule on VMC on AWS Console and ensure that you’ve correct rule created to allow Incoming and Outgoing Traffic Flow between RDS DB Instance and Application Server. Also ensure there’s HTTP/HTTPS rule that allows Any traffic to request web traffic. Below rules are applied to “All Uplinks” which includes “VPC Interface” for communication between AWS Services including Amazon RDS.
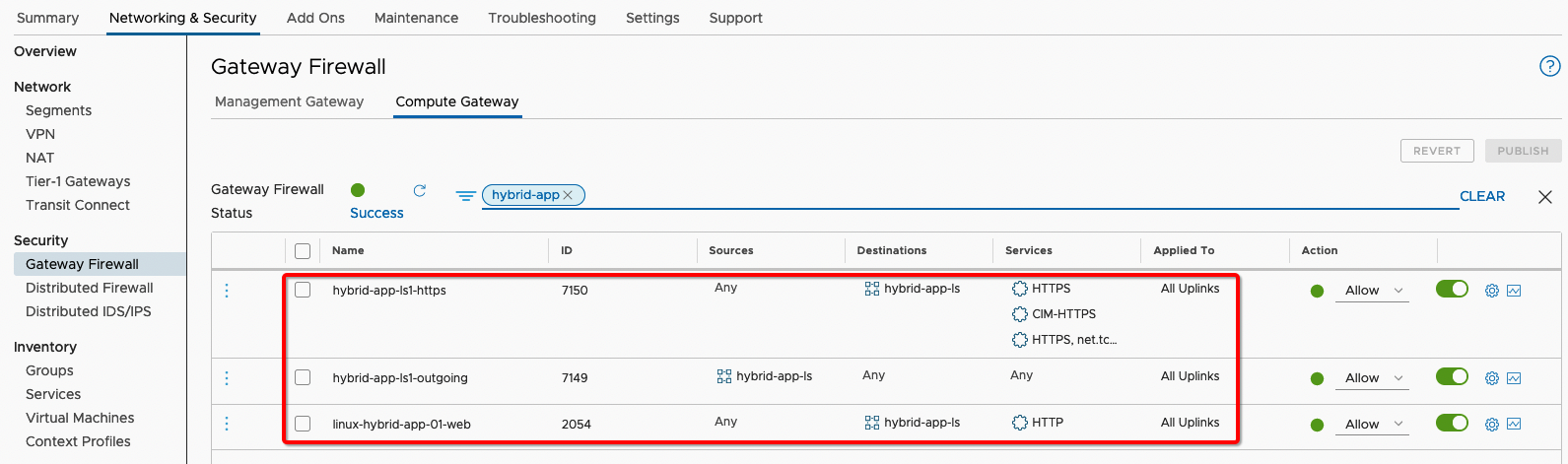
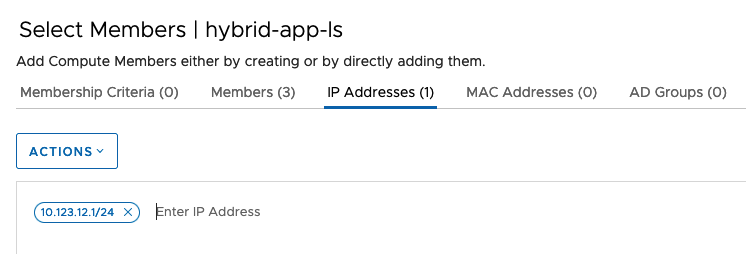
a) “hybrid-app-ls” is a group that has 10.123.12.1/24 as its IP range, the application server “linux-hybrid-app01” is part of this CIDR range.
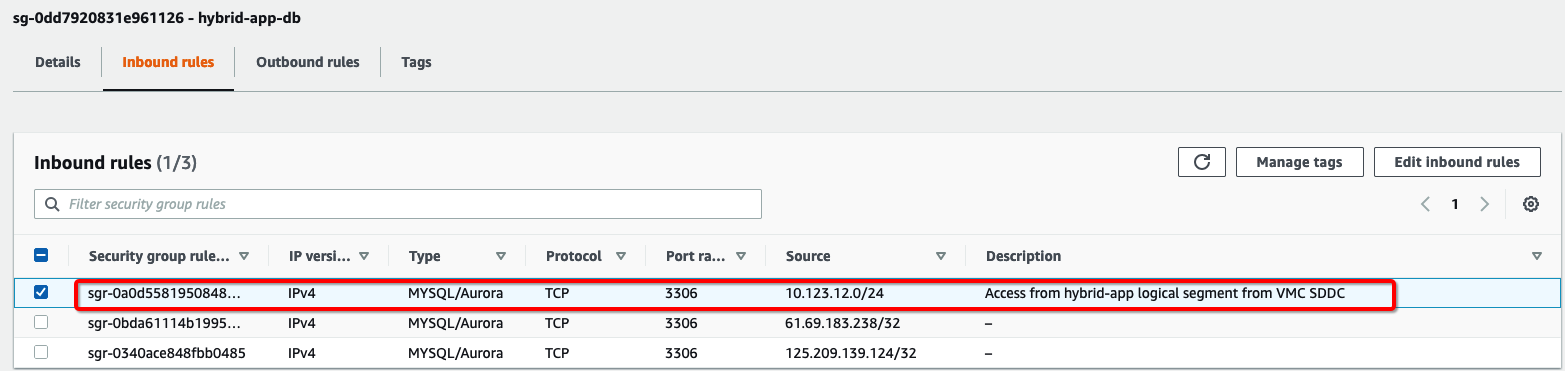
5. Configure Firewall/Security Group Rules to allow traffic flow between Amazon RDS Instance “hybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com” and Application Server “linux-hybrid-app01”.
a) Configure Security Group Rules associated with Amazon RDS DB Instance in AWS Web Console and ensure its Inbound Rule has correct entry for 10.123.12.0/24 on port 3306.
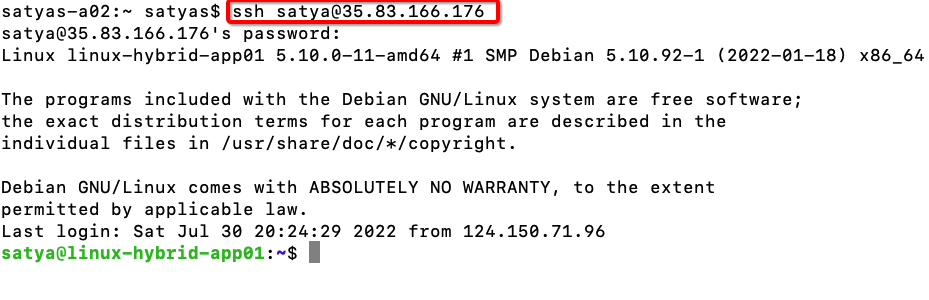
6. Once the above steps are complete, confirm you can access the “linux-hybrid-app01” server publicly. Below we’re creating an SSH session with the “linux-hybrid-app01” server.
7. Since we are using WordPress Application for Front End, install WordPress application with the below steps:
a) Install Apache:
apt install apache2
b) Install PHP:
apt install php libapache2-mod-php php-mysq
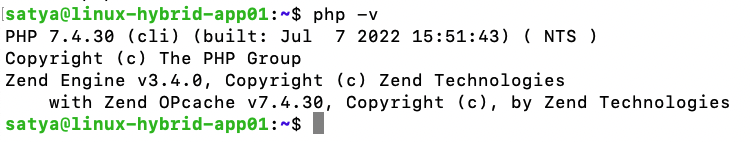
c) Check PHP Version:
php -v
d) Download, Install and configure WordPress application:
Go to Document Root Directory of Apache
cd /var/www/html
Download WordPress:
wget http://wordpress.org/latest.tar.gz
Extract content of downloaded tar file:
tar xfz latest.tar.gz
Move everything from the WordPress folder to the Apache document root folder:
mv wordpress/* ./
Remote downloaded tar file and old index.html file:
rm -f latest.tar.gz
rm index.html
Make wp-content directory writeable to www-data:
cd /var/www/html/
chown -R www-data:www-data wp-content
Create uploads folder and make it writeable to the WordPress application:
mkdir uploads
chmod 755 -R uploads
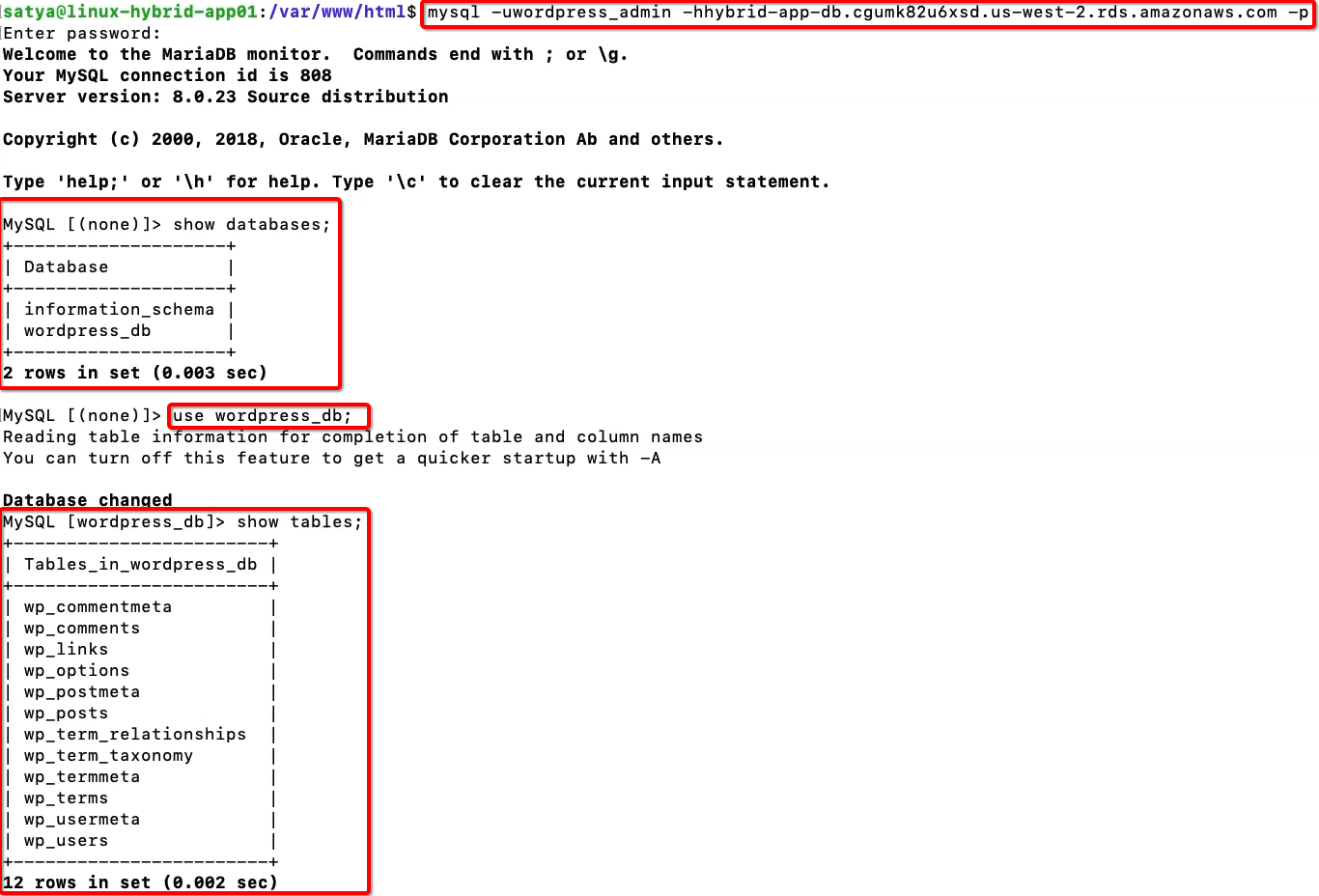
8. Connect to Amazon RDS DB Instance and Create a WordPress Database and WordPress user for WordPress application.
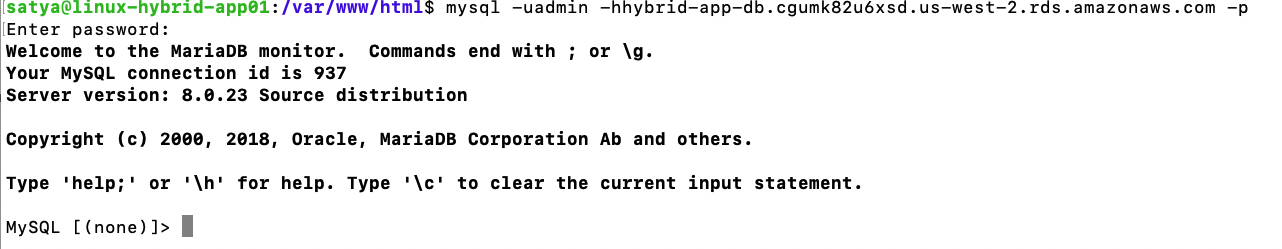
a) Connect to RDS DB Instance as an admin user:
mysql -uadmin -hhybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com -p
CREATE DATABASE wordpress_db;
c) Create a user for WordPress and provide appropriate permissions:
CREATE USER 'wordpress_admin'@'localhost' IDENTIFIED BY 'P4ssw0rd!';
GRANT ALL PRIVILEGES ON wordpress_db.* TO 'wordpress_admin'@'localhost';
FLUSH PRIVILEGES;
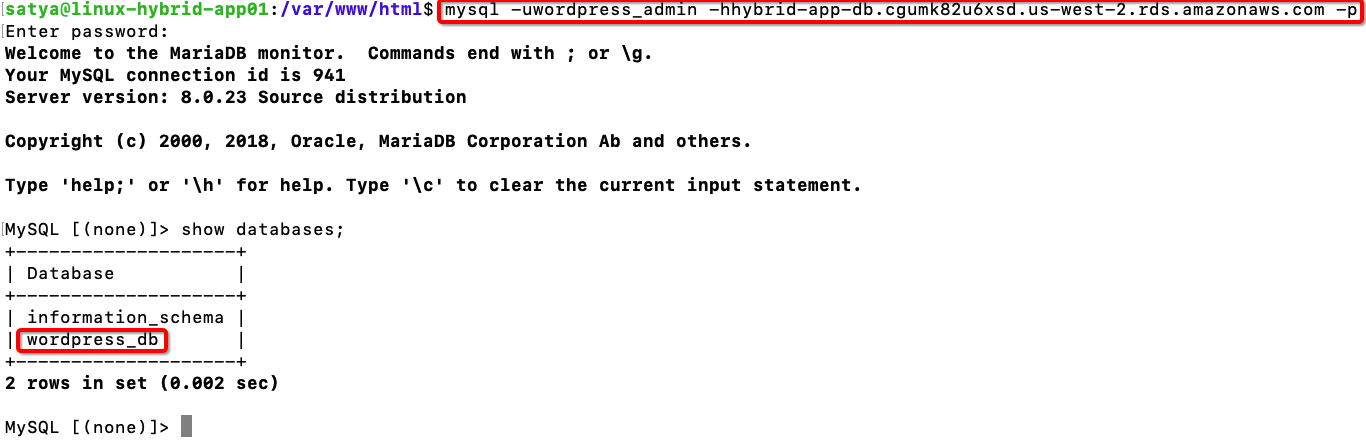
d) Check if wordpress_admin user can connect to Amazon RDS DB Instance:
mysql -uwordpress_admin -hhybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com -p
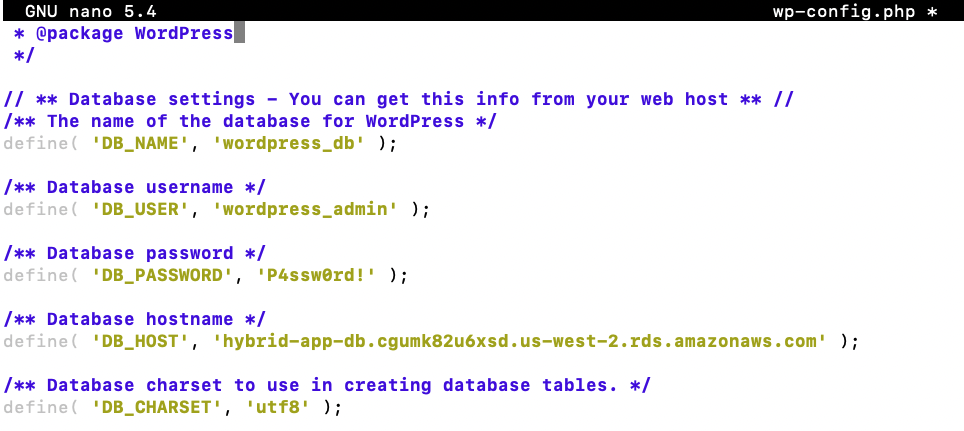
9. Update Database Connection Configuration for WordPress application to use Amazon RDS DB Instance “hybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com” and appropriate WordPress user we created above by modifying wp-config.php file:
cp wp-config-sample.php wp-config.php
Update wp-config.php file as below:
nano wp-config.php
define( 'DB_NAME', 'wordpress_db' );
/** MySQL database username */
define( 'DB_USER', 'wordpress_admin' );
/** MySQL database password */
define( 'DB_PASSWORD','P4ssw0rd!' );
/** Database hostname */
define( 'DB_HOST', 'hybrid-app-db.cgumk82u6xsd.us-west-2.rds.amazonaws.com' );
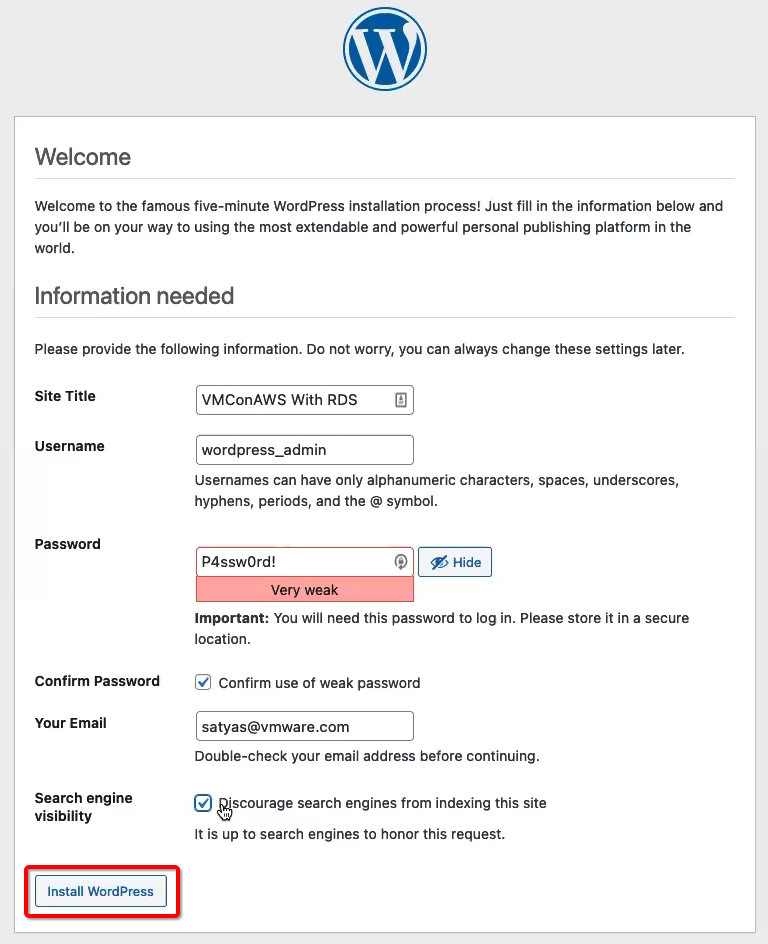
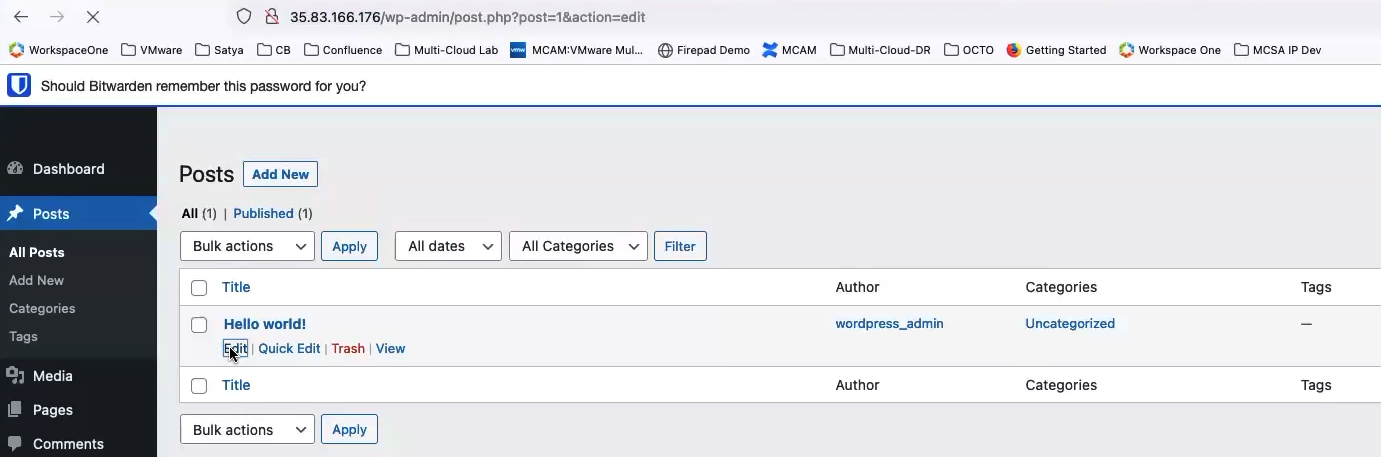
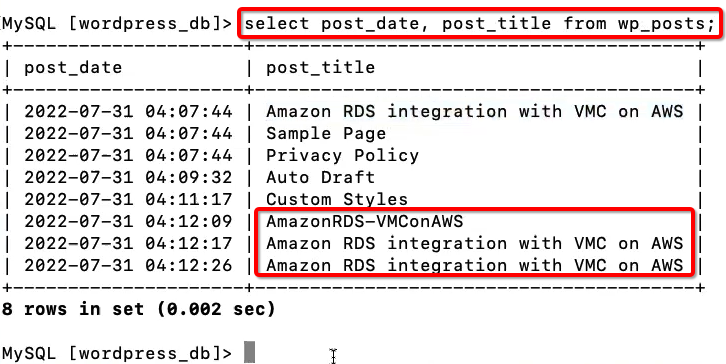
Below select statement shows the updated post is being appropriately saved in the WordPress database in Amazon RDS DB Instance.
And That’s It. We’ve successfully Integrated Amazon RDS with workload running on VMC on AWS SDDC. Hope you find this post useful. Comments and suggestions are welcome.
Satya is an experienced IT professional with a demonstrated history of working in the Information Technology with years of experience in multiple industry verticals. He currently works for VMware as Staff Cloud Solutions Architect. He is skilled in designing and implementing Enterprise Application Suite in Public, Private and Hybrid cloud infrastructure including AWS, VMware, VMware Cloud on AWS, Microsoft Azure, Google Cloud and the like.
Get connected with Satya:




0 Comments