Knowledge Academy
Advancing Knowledge, Transforming Lives
5 Questions to Think About When Reviewing your Backup and Data Management Strategy …
The following list of questions is not exhaustive however, I find them to be the most relevant when discussing the topic of backup and data management with organizations that are evaluating their existing backup strategy : 1. Where does your...

Why go SaaS for your Backup and Recovery Solution ?
Being in the IT industry over the last 19 years, I have seen and worked with a fair share of backup and disaster recovery solutions over the years. Life has not always been kind to the System Admins that begrudgingly shoulder the responsibility of...
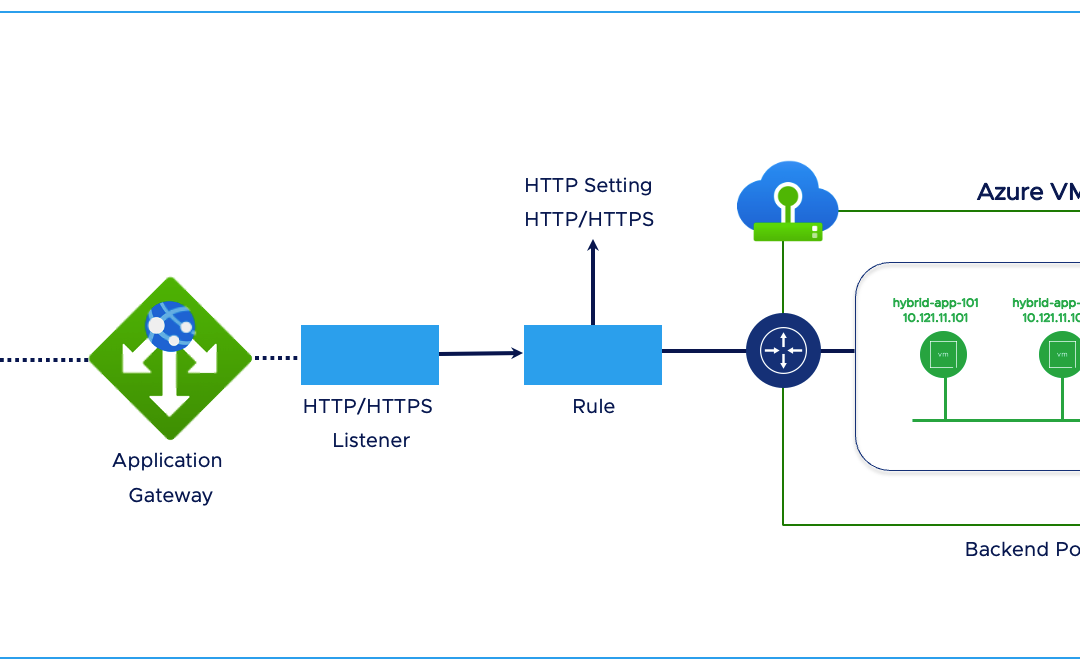
Load Balancing Azure VMware Solution workloads with Azure Application Gateway
Brief Introduction to Azure VMware SolutionWith Azure VMware Solution (AVS), now available globally in Microsoft Azure as a native Azure Cloud offering from Microsoft, customers around the globe can enjoy the same world class industry leading...

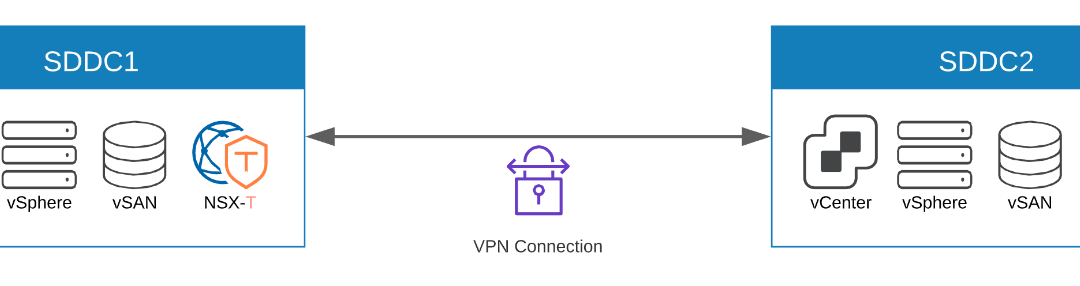
Creating Cloud to Cloud Policy Based IPSEC VPN between two SDDC on VMware Cloud on AWS
VPN is a basic networking construct when it comes to connecting multiple sites privately. Be it a private network connection from one on-premise site to another on-prem site, or a connection from an on-prem site to VMware Cloud on AWS SDDC (or vice versa), or even to establish private connections between VMware Cloud on AWS SDDC to another VMware Cloud on AWS SDDC.
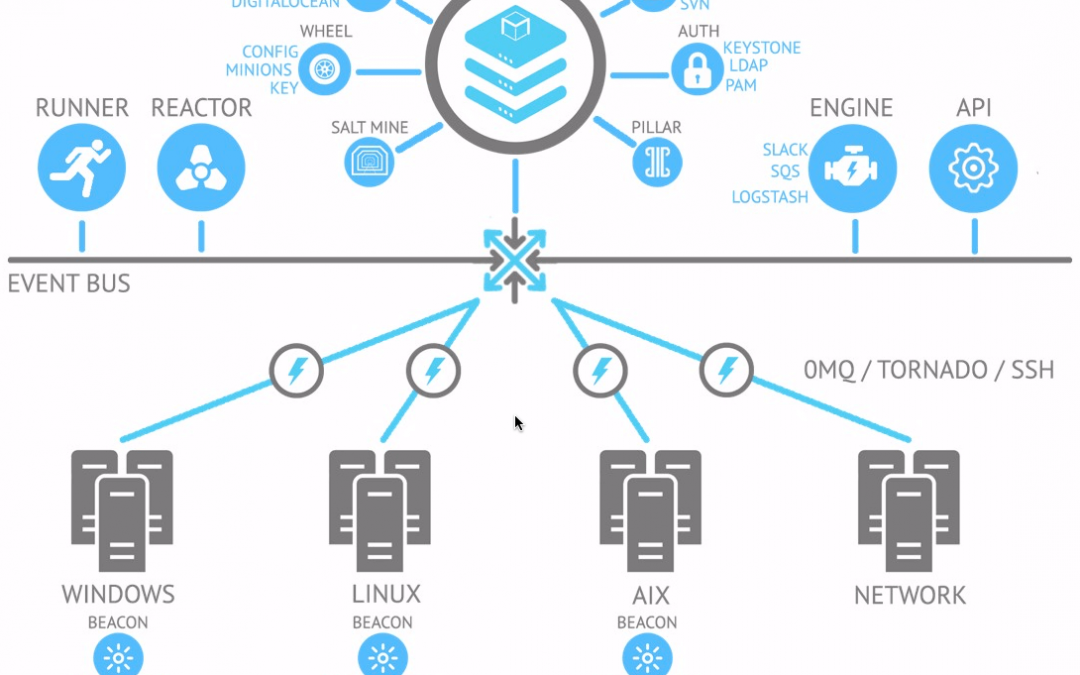
Saltstack
Saltstack Introduction: Salt is a Python-based open-source remote execution framework used for: Configuration management Automation Provisioning Orchestration Salt uses the master-client model in which a master issues commands to a client and the...

Encrypting Systems Manager Sessions
I recently discovered that we can encrypt ec2 sessions launched via AWS Systems Manager. I figured it needs a few things in place to make it happen, A KMS key to be used for encrypting sessions with the following policy attached to it. Refrence...
Creating VMware Clouds in Multiple Clouds
As VMware forges partnership with our Public Cloud Provider Partners (also known as Hyperscale partners), our customers now have choice and flexibility to choose the appropriate Public Cloud Providers, in their preferred geographic region, to...
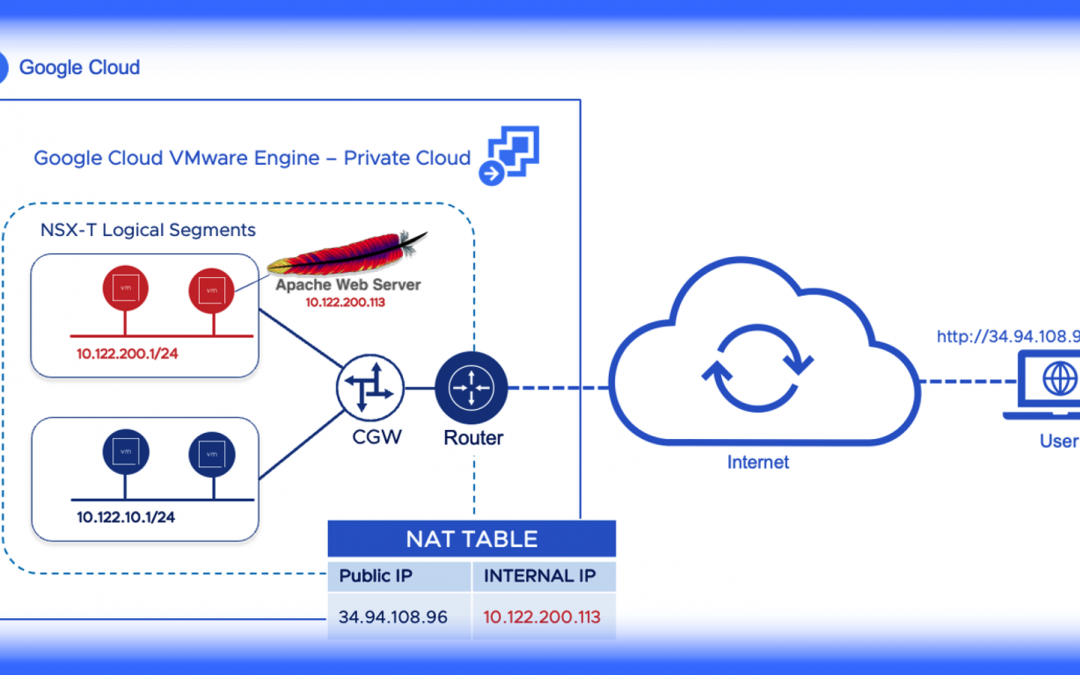
Assigning Public IP Addresses to Workloads on Google Cloud VMware Engine (GCVE)
In GCVE, the public IP address network service enables external access to virtual machines, management appliances, and load balancers running within your private cloud. By default, this service is deactivated in GCVE. In many cases, it may be...

Future of Technologies: Blockchain
"Everything will be tokenized and connected by blockchain one day" - Fred Ehrsam Blockchain was invented by group of people using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the crypto currency Bitcoin.What really...
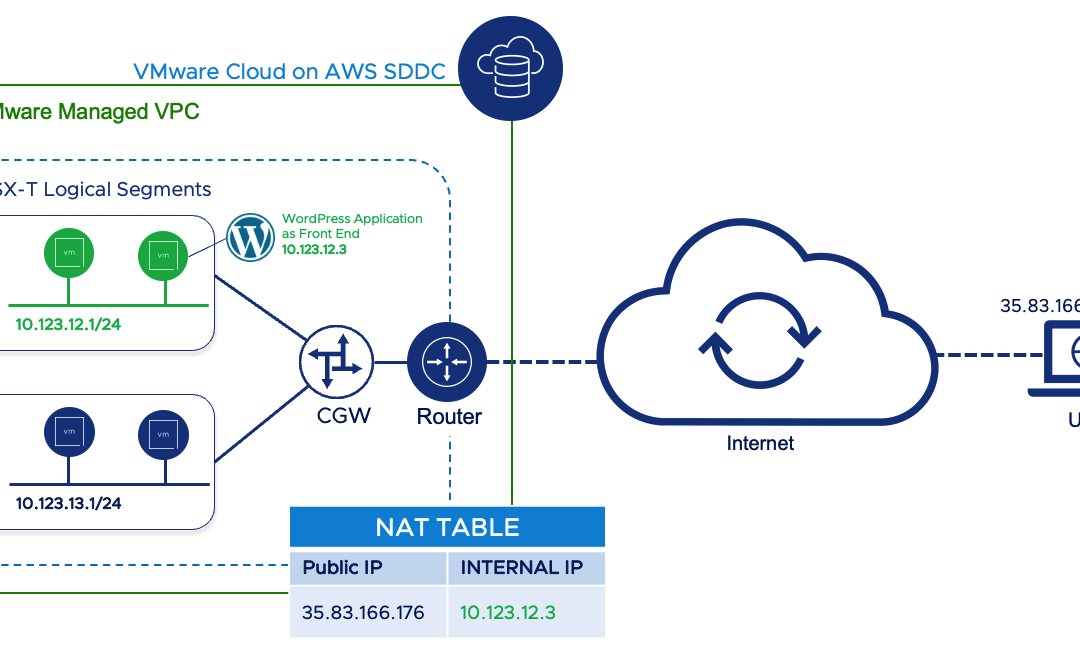
Assigning Public IP to Workloads running on VMware Cloud on AWS
In certain situations, it may be necessary to assign a public IP address directly to a workload running on VMware Cloud on AWS. One of the major use case for assigning a public IP address to a virtual machine (VM) in VMware Cloud on AWS is to...
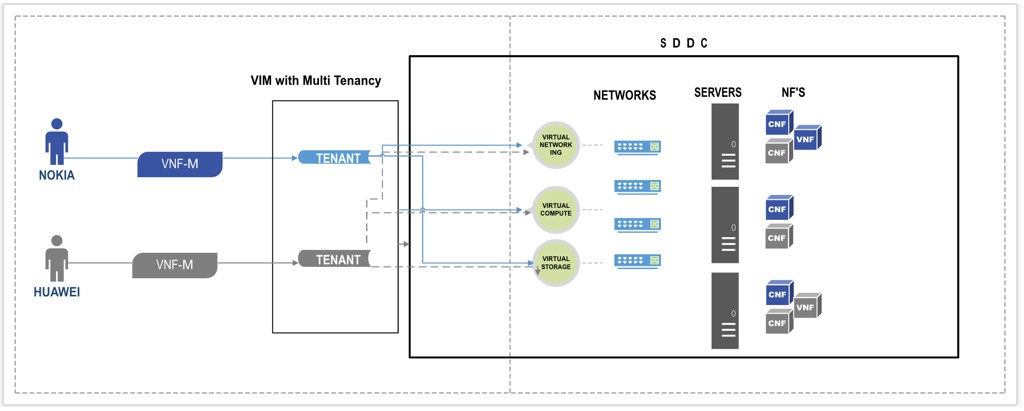
Multi Tenancy in Telco Space
Praveen Batta is a senior consultant and CTO-Ambassador at VMware. Serving the Telco Industry, focusing on Kubernetes, cloud technologies, and VMware solutions. He has 16 years of experience in multiple technologies, including:...
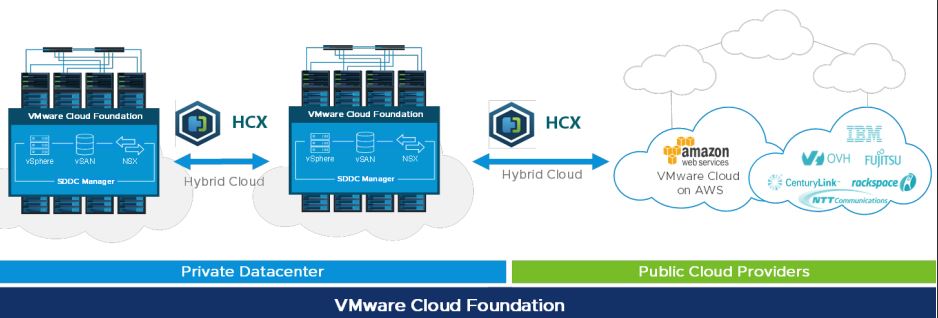
Migrating to VMware Cloud
As we discussed earlier, Cloud Migration is an important aspect while adopting Public Cloud Infrastructure and it is this area where organizations put in lots of effort to mitigate the risk and reduce the disruptions caused to the business. VMware...
SDDC Groups with VMware Transit Connect™
VMC on AWS SDDC Version 1.12 release brings many new exciting features to our customers. With this release, SDDC networking becomes easier to manage, more scalable, and performant with the VMware Transit Connect™. This feature was in Preview...
How to Access AWS S3 Buckets from EC2 Instances
What is the S3 Bucket? AWS S3 bucket is a directory/folder where we can store any kind of data except application or OS. Why AWS called S3 bucket for directory/folder because bucket has " Sx3" Simple Storage Service. In S3 bucket we can store any...
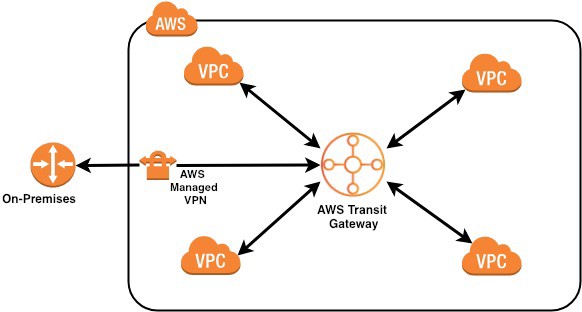
Networking Architecture – Hybrid
Yet another interesting architecture including AWS services like AWS Site-to-Site VPN, PrivateLink and Transit Gateway. This solution enables connectivity between a Corporate Data Center and workloads deployed in AWS Environment. Let’s say we want...
Inviting a new user to VMware Cloud (VMC) on AWS Organisation
VMware Cloud on AWS supports a well-defined Role-Based Access Control (RBAC) model. In a VMware Cloud on AWS Organisation, there are two roles available, namely: Organization Member and Organization Owner. Only the Organization Owner can invite...

Digging deep into dig command
DIG stands for Domain Information Groper. As the name suggests it is used to grab information from a DNS server. It is one of the most powerful yet most underrated utility. Sometimes we get overwhelmed by all the information that is shown and...
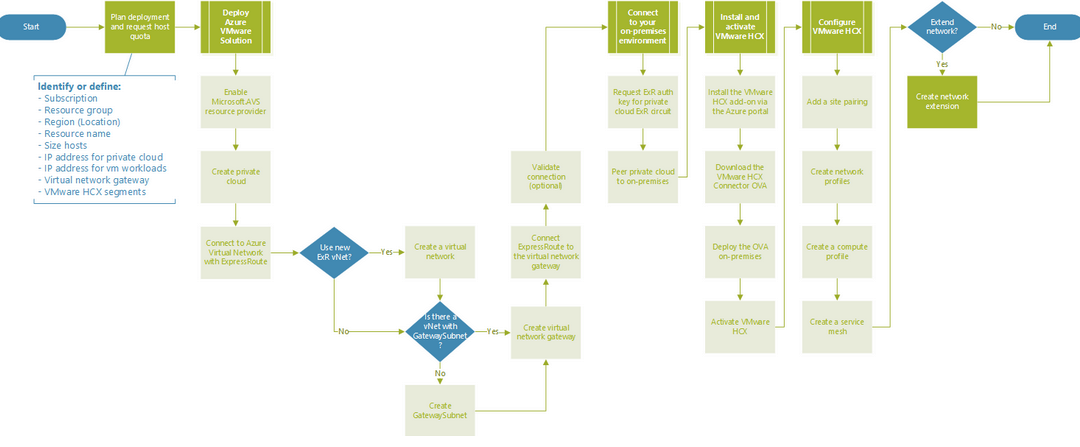
Integrate Azure Files with Azure VMware Solution
Azure VMware Solution is a VMware validated solution with on-going validation and testing of enhancements and upgrades. Microsoft manages and maintains private cloud infrastructure and software. It allows customers to focus on developing and...

5 Questions to Think About When Reviewing your Backup and Data Management Strategy …
The following list of questions is not exhaustive however, I find them to be the most relevant when discussing the topic of backup and data management with organizations that are evaluating their existing backup strategy : 1. Where does your...

Why go SaaS for your Backup and Recovery Solution ?
Being in the IT industry over the last 19 years, I have seen and worked with a fair share of backup and disaster recovery solutions over the years. Life has not always been kind to the System Admins that begrudgingly shoulder the responsibility of...

Load Balancing Azure VMware Solution workloads with Azure Application Gateway
Brief Introduction to Azure VMware SolutionWith Azure VMware Solution (AVS), now available globally in Microsoft Azure as a native Azure Cloud offering from Microsoft, customers around the globe can enjoy the same world class industry leading...

Creating Cloud to Cloud Policy Based IPSEC VPN between two SDDC on VMware Cloud on AWS
VPN is a basic networking construct when it comes to connecting multiple sites privately. Be it a private network connection from one on-premise site to another on-prem site, or a connection from an on-prem site to VMware Cloud on AWS SDDC (or vice...

Saltstack
Saltstack Introduction: Salt is a Python-based open-source remote execution framework used for: Configuration management Automation Provisioning Orchestration Salt uses the master-client model in which a master issues commands to a client and the...

Encrypting Systems Manager Sessions
I recently discovered that we can encrypt ec2 sessions launched via AWS Systems Manager. I figured it needs a few things in place to make it happen, A KMS key to be used for encrypting sessions with the following policy attached to it. Refrence...

Creating VMware Clouds in Multiple Clouds
As VMware forges partnership with our Public Cloud Provider Partners (also known as Hyperscale partners), our customers now have choice and flexibility to choose the appropriate Public Cloud Providers, in their preferred geographic region, to...

Assigning Public IP Addresses to Workloads on Google Cloud VMware Engine (GCVE)
In GCVE, the public IP address network service enables external access to virtual machines, management appliances, and load balancers running within your private cloud. By default, this service is deactivated in GCVE. In many cases, it may be...

Future of Technologies: Blockchain
"Everything will be tokenized and connected by blockchain one day" - Fred Ehrsam Blockchain was invented by group of people using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the crypto currency Bitcoin.What really...

Assigning Public IP to Workloads running on VMware Cloud on AWS
In certain situations, it may be necessary to assign a public IP address directly to a workload running on VMware Cloud on AWS. One of the major use case for assigning a public IP address to a virtual machine (VM) in VMware Cloud on AWS is to...

Multi Tenancy in Telco Space
Praveen Batta is a senior consultant and CTO-Ambassador at VMware. Serving the Telco Industry, focusing on Kubernetes, cloud technologies, and VMware solutions. He has 16 years of experience in multiple technologies, including:...

Migrating to VMware Cloud
As we discussed earlier, Cloud Migration is an important aspect while adopting Public Cloud Infrastructure and it is this area where organizations put in lots of effort to mitigate the risk and reduce the disruptions caused to the business. VMware...

SDDC Groups with VMware Transit Connect™
VMC on AWS SDDC Version 1.12 release brings many new exciting features to our customers. With this release, SDDC networking becomes easier to manage, more scalable, and performant with the VMware Transit Connect™. This feature was in Preview...

How to Access AWS S3 Buckets from EC2 Instances
What is the S3 Bucket? AWS S3 bucket is a directory/folder where we can store any kind of data except application or OS. Why AWS called S3 bucket for directory/folder because bucket has " Sx3" Simple Storage Service. In S3 bucket we can store any...

Networking Architecture – Hybrid
Yet another interesting architecture including AWS services like AWS Site-to-Site VPN, PrivateLink and Transit Gateway. This solution enables connectivity between a Corporate Data Center and workloads deployed in AWS Environment. Let’s say we want...

Inviting a new user to VMware Cloud (VMC) on AWS Organisation
VMware Cloud on AWS supports a well-defined Role-Based Access Control (RBAC) model. In a VMware Cloud on AWS Organisation, there are two roles available, namely: Organization Member and Organization Owner. Only the Organization Owner can invite...

Digging deep into dig command
DIG stands for Domain Information Groper. As the name suggests it is used to grab information from a DNS server. It is one of the most powerful yet most underrated utility. Sometimes we get overwhelmed by all the information that is shown and...

Integrate Azure Files with Azure VMware Solution
Azure VMware Solution is a VMware validated solution with on-going validation and testing of enhancements and upgrades. Microsoft manages and maintains private cloud infrastructure and software. It allows customers to focus on developing and...




Recent Comments