Legacy networks are based on hardware whereas 5G networks are based on virtualization.
Network slicing is one of the key enabling technology which Is playing critical role in 5G space to deliver the guaranteed QoS requirements.
Network slicing is originated from the concept of network sharing and 3GPP has developed the standards for the same.
Network slicing is the concept of sharing the networks on a shared infrastructure and draw a logical network. This comprises of needed configurations for that particular business like defined network resources, QoS, security policies etc.
There are multiple slice types which are standardized called Slice service type (SST). Below is the list of them.
- eMBB - Enhanced Mobile BroadBand
- mMTC - massive Machine Type Communication
- uRLLC - Untra Reliable Low Latency Communication
- V2X - Vehicle to everything and everything to vehicles
- HMTC - High-performance Machine Type Communications
There is a possibility to use optional and nonstandard slice types also. Make a not that these are organization specific. They are called Slice Differentiator (SD)
Few examples:
- Smart agriculture can use mMTC slices
- Smart building with video surveillance can use eMBB
- AR-VR tactile application’s, Industrial automation with robot control may demand for uRLLC.
Implementation:
Implementation of Network slicing can be planned in multiple phases/stages.
Phase 1 -
Providers design based on capacity or on the forecast of the application usage.
We are going to define the characteristics of the network slice. Understand the NF (Network Function) and its requirements to implement the network slicing in a better way.
For example: V2X may be latency-sensitive and need accuracy. V2X is for vehicles to communicate with everything and vice versa. Whereas web browsing applications may not demand throughput/latency.
In this example, the V2X standard slice can be preferred for V2X use cases. And eMBB standard network slice (with characteristics like capacity, # users etc) can be preferred for web browsing applications. And inside that each network (Core, RAN, Transport) will be requesting different network slices.
Phase 2 -
Implementation happens on-demand basis. This handles multiple varieties of network slices with distinctive characteristics.
For example: A service provider wants to create a networking for transport domain, network slices are created according to the requirements of that transport domain.
Phase 3 -
Implementation happens on tenant based. Here a further deeper level of network slicing happens based on tenants and respective customer requirements.
Considering the example of Phase 2, here in phase 3 - network slices are created for a particular customer in the transport domain like Fedex.
These slices in phase 3 will be ephemeral.
Multi-tenancy and network slicing
The purpose of multi tenancy came into the picture when we want to share the resources between different parties. That can be infrastructure (IaaS), software (SaaS) or Platform (PaaS).
A multi-tenant architecture is based on central administration, and involves a common code application, operating common instance(s) of applications for multiple tenants. In addition, it also secures private data for each tenant from others.
Multi-tenancy is necessary to share the same resources within the data-center. All tenants will share the compute, storage and network resources with provided security and access restrictions. Here we are going to cover network sharing and how that is going to address the network resources.
Different tenants can use various network slices which are bound with a set of network policies and security rules.
This provides desired throughput, latency, and security to the respective tenants.
For example, a customer service provider (CSP) needs to serve multiple customers with different set of requirements. CSP can still use the same networking setup on the premises and create different network slices for each customer. Each network slice will be configured with required QoS (Quality of Service).
Let's consider the mobile networks requirements. Some networks may demand for lower latency to serve their network functions like CUPS, UPF etc. And some other networks may demand for better band width. Each requirement will be addressed by each network slice on the same physical environment.
With this approach, CSP's are also reducing CAPEX (Capital Expenditure) and OPEX (Operational Expenditure) and gaining huge advantages with lower entry costs like starting with lower cost and growing big. Another advantage of multi-tenancy is scalability.
Now 5G is dependent on virtualization. Operators demand various classes of traffic for data and voice for different use cases like self-driving cars, sensor devices, web services etc and with different SLA's. Your networking capabilities are playing key responsibility here.
Below picture will give the high-level view of how tenants and network slices work together in cloud environments.
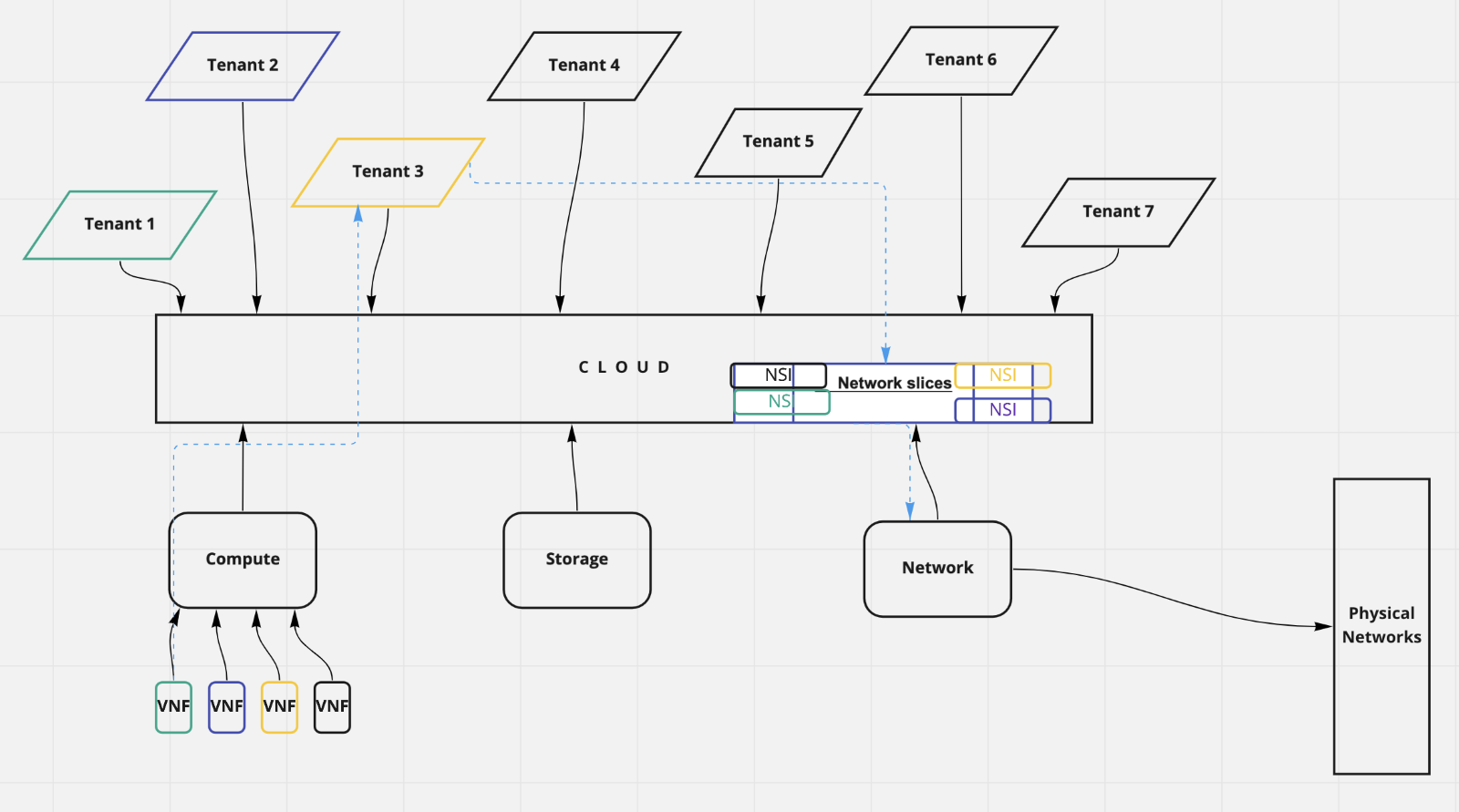
See the possibilities of - Tenants accessing their respective network slice's, multiple tenants accessing their respective network slice, and single-tenant accessing multiple network slices.
Let's look at a simple example: There is an ISP (Internet service provider) that provides network services to different vendors. In this below example Industrial, Hospital and transport are the vendors.
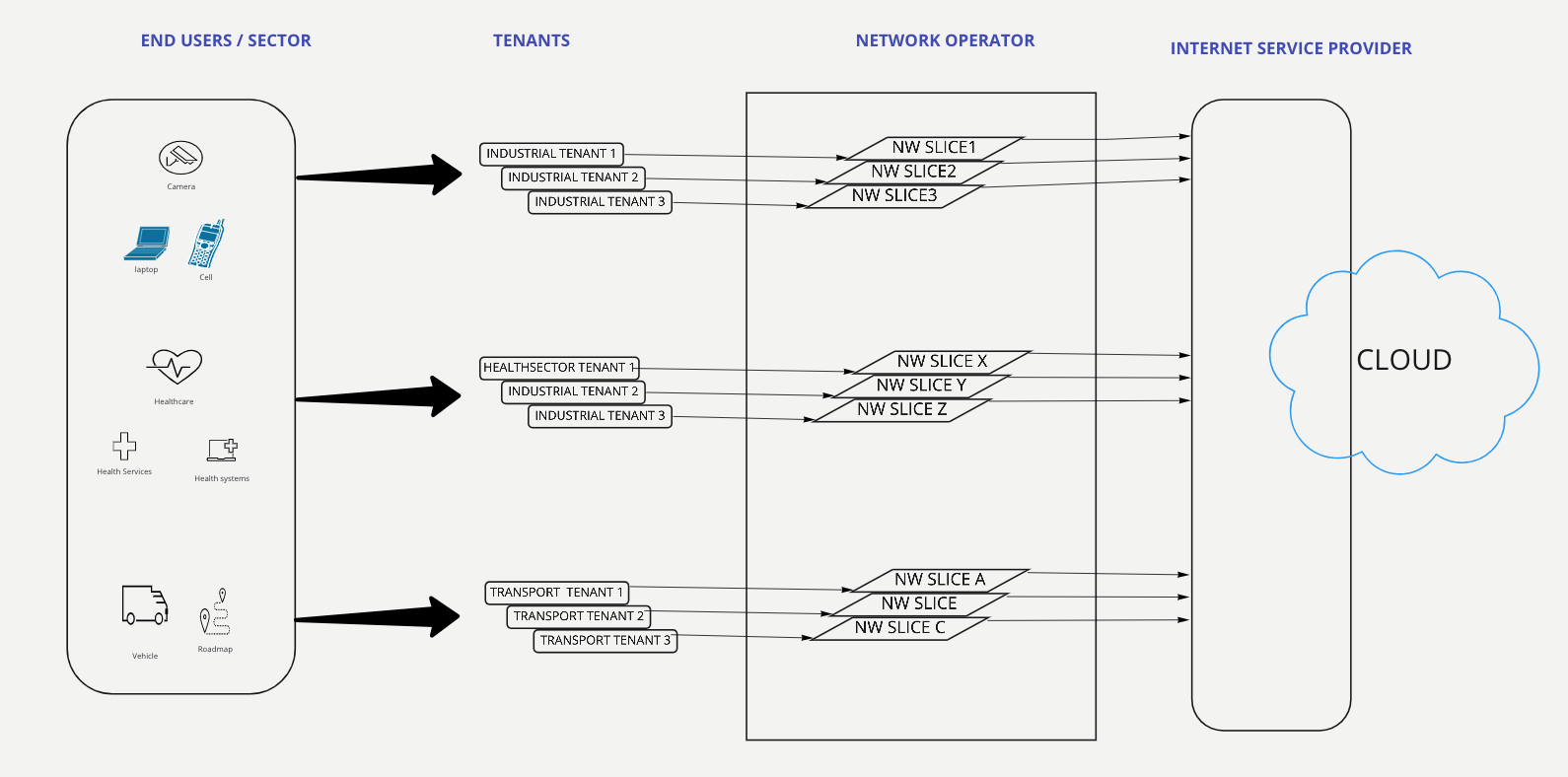
Network slices created for Industrial will be accessed by the tenants "company offices", "Factories", "Workshop" i.e multiple tenants accessing multiple network slices. And the same logic applies to the remaining 2 sectors too.
No two sectors can talk to each other. In this way network isolation is achieved along with interconnectivity. All these configurations are scalable and dynamic.




0 Comments